Learn why scanning applications in the repository is crucial for application security. Shift left to detect and fix vulnerabilities.

Learn why scanning applications in the repository is crucial for application security. Shift left to detect and fix vulnerabilities.
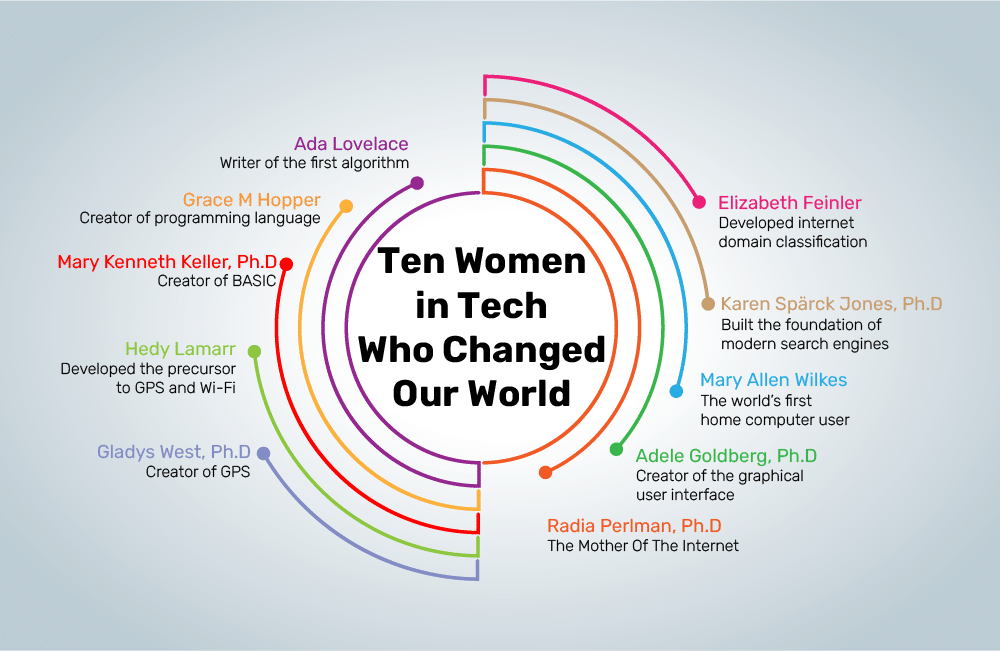
Discover ten pioneering women in tech who changed the world. Learn about their visionary work and revolutionary outcomes.
Learn about the implications of shifting applications to the cloud on application security. Understand the shared responsibility.

Learn how the Fintech sector can tackle vulnerabilities like Spring4Shell with speed and efficiency using the Mend platform.
Discover the key principles of modern application security. Learn how to secure your software and protect against evolving threats.
Learn about Kubernetes Security Best Practices, a crucial aspect of managing containerized workflows at scale.

Discover how Mend’s talented women in tech are leading the way in application security and community. Insights, advice, and career highlights.

Explore the state of open source in financial services with FINOS. Discover key findings on adoption, benefits, challenges.

Explore the complexities of application security responsibility in the age of DevSecOps and supply chain breaches. Who should take the lead?
Learn how to enhance your application security program with tips from “The CISO’s Guide to Application Security Innovation.”

Learn how to build a modern AppSec strategy to secure applications in the face of evolving threats. Explore tactics, trends, and best practices.
Learn about the challenges and best practices of securing Docker containers, and why securing containers is vital for application security.
Learn how to effectively manage risk in cloud-native environments. Explore the vulnerabilities, risks, and best practices for security.

Building a modern application security strategy is crucial in today’s threat landscape. Learn about threats, opportunities, and challenges.
Discover why a new approach to SAST is essential for modern businesses. Learn the pros and cons of old and new SAST tools.
Learn about the threats to Kubernetes security and how to protect your containerized applications.