Forrester’s State of Application Security, 2020: Key Takeaways

Table of Contents
In The State of Application Security, 2020, Forrester predicts application vulnerabilities will continue to be the most common external attack method. Because of this, organizations are urged to continue testing early in the software development life cycle (SDLC), implementing auto-remediation for security vulnerabilities, and shoring up production protections. To learn more, we’ve put together an overview of Forrester’s report to provide you with the key takeaways for application security.
Applications continue to be the weakest link
As applications become more complex, rely on third-party libraries, and support new frameworks, they become more vulnerable to security threats. In a survey of security professionals, the majority of external attacks were carried out either by exploiting a software vulnerability (42%) or through a web application (35%).
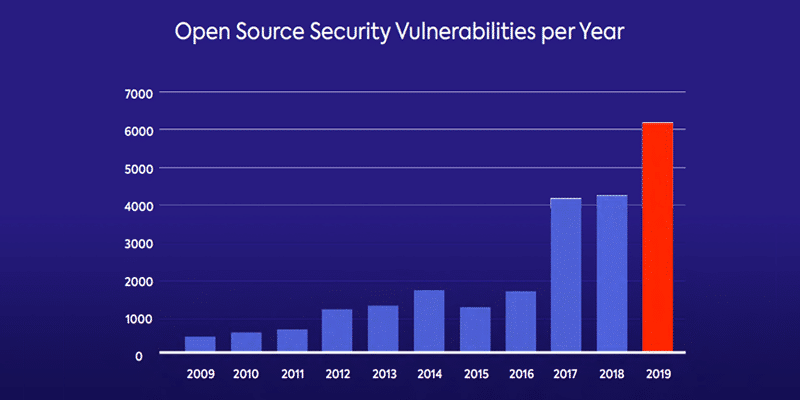
Forrester cited open source software as a chief concern for application security. Although open source software allows development teams to code faster while focusing on their own core expertise, it remains as vulnerable as it is pervasive. In fact, open source security vulnerabilities have risen by 50% since last year.
The rise of new architectures and frameworks also creates risk as they provide new attack surfaces. Security professionals must now worry about things like unsecured APIs, image integrity, and changes to containers and functions in production.
No doubt developers are moving faster than ever before. More than one-third of developers are releasing new features or updates on a monthly basis or faster. Security must keep up. Any security tools and processes that don’t will be left behind.
More security is needed throughout the SDLC
Despite the risk posed by applications, only 14% of organizations fully integrate security throughout their SDLC. For organizations just beginning to address security in the SDLC, most are implementing security at the testing stage. In order to protect their applications, organizations are encouraged to shift left to earlier development and design stages when it comes to security.
Despite this grim news that not enough organizations are fully integrating security into their SDLC, Forrester does see several encouraging trends. First is the rise in popularity of interactive application security testing (IAST) at the expense of dynamic application security testing (DAST) tools. Moving to IAST helps teams embed security into their existing development processes more effectively than DAST.
Second, software composition analysis (SCA) tools, which automate visibility into open source inventory to assess security risk and license compliance, are being implemented in development phases at about the same rate as they are being implemented during testing. This signals a trend toward shifting left. Organizations will benefit from implementing SCA earlier in development to help prioritize and remediate open source vulnerabilities.
Finally, container security is shifting to earlier development stages too. According to Forrester data, in the coming year, 37% of security professionals plan to implement container security during development, and 20% plan to implement it during design.
Embrace automation
Forrester strongly recommends organizations embrace automation in testing and remediation, which reduces vulnerabilities overall while also educating developers in real time. By integrating automated application security testing tools into the CI/CD pipeline, scans can be run continuously on check-in, build, and integration to make remediation quick and cost-effective. Auto-remediation will also help scale your development and security resources by reducing time-to-fix.
Don’t get complacent
Because of the security risk posed by applications, it is important to invest in security that aligns closely with the development process. Forrester outlines several ways in which to accomplish this:
- Ensure your security policies cover open source and container images, and use SCA and container security tools.
- Developer security champions should be used to extend security’s reach and train developers throughout your organization.
- Software development policies and training must support auto-remediation tools.
By following the path of seasoned security professionals, you can mitigate your organization’s risk. Now is not the time to backslide on application security.


