Automated Software Supply Chain Attacks: Should You be Worried?

Table of Contents
From the factory floor to online shopping, the benefits of automation are clear: larger quantities of products and services can be produced much faster. But automation can also be used for malicious purposes, as illustrated by the ongoing software supply chain attack targeting the NPM package repository. By automating the process of creating and publishing malicious packages, the threat actor behind this campaign has taken things to a new scale. The malicious modules, which target Azure and Uber developers among others, use techniques such as dependency confusion to retrieve private user information.
The packages related to this attacker were detected and blocked by Mend Supply Chain Defender within minutes of their release, and all were reported to NPM. Mend research teams continuously monitor, detect, block, and report these packages and similar malicious modules.
This is part of an extensive series of guides about software supply chain security.
Automated Software Supply Chain Attacks: Overview
As of March 31, 2022, the Mend security teams have observed the publication of more than 900 malicious packages by this threat actor who started publishing malicious packages on February 23, 2022 . That breaks down to an average of nearly 25 packages per day, making this one of the largest malicious campaigns seen to date. As of the date this blog was published (March 31, 2022), the malicious campaign is ongoing . Indeed, it seems as though the threat actor is well-aware of recent media attention, as one of the latest packages released was named “helloscanners4.”
While we observed the first malicious package released by the actor on February 23, we suspect that this is not their first rodeo. At least one of the packages used by the attacker was previously associated with a malicious attack launched on September 30, 2021, in a malicious package named azure-api-style-guide, version 2.0.1 that has already been taken down from NPM registry. Although we can’t definitively confirm that the two attacks originate from the same actor, it does establish a pattern of use.
The attacker has also continued to modify the malicious coding over the course of this campaign. For example, in the version released on March 30, 2022, we see obfuscation of the code. In another package called serotonine320 that was released April 1, 2022, we see the obfuscated code in the README file. It’s also worthwhile to note that the attacker is releasing empty packages along with the malicious modules. While that may seem innocuous at first glance, that is not really the case. Empty packages can serve as a back door to threat actors, who can upload malicious content into the package at a later date. They therefore should be treated as unwanted code and removed.
Should you be worried about Automated Software Supply Chain Attacks?
The attack vector used by this malicious actor is both widely known and frequently used. What’s new about this is the scale of the attack. By applying automation to the process, the attacker was able to generate a very large number of malicious packages, as well as more easily sustain the attack over time.
But other than the large attack scale (and subsequent public attention) which created a lot of noise, does this attack campaign warrant extra precaution? The answer is no — keep the usual precautions with npm packages.
A little perspective helps explain why. In the past three months, Mend Supply Chain Defender found more than 2,000 malicious packages within NPM, meaning that there were more than 1,100 malicious packages that were unrelated to this campaign. The reality is that attackers publish malicious packages in NPM on a daily basis, and many of them use the same exfiltration methods deployed in this campaign. We also see many cases where obfuscation techniques are used.
Let’s quickly take a look at dozen packages generated by four different actors over the past couple of months:
We will start with two packages from March 30, 2022: tb3003 and colors-1.0-v-1.4.0
Examples of Software Supply Chain Attacks
Example 1
tb3003 is straightforward one-line code that uses interactsh to exfiltrate private user information.
Example 2
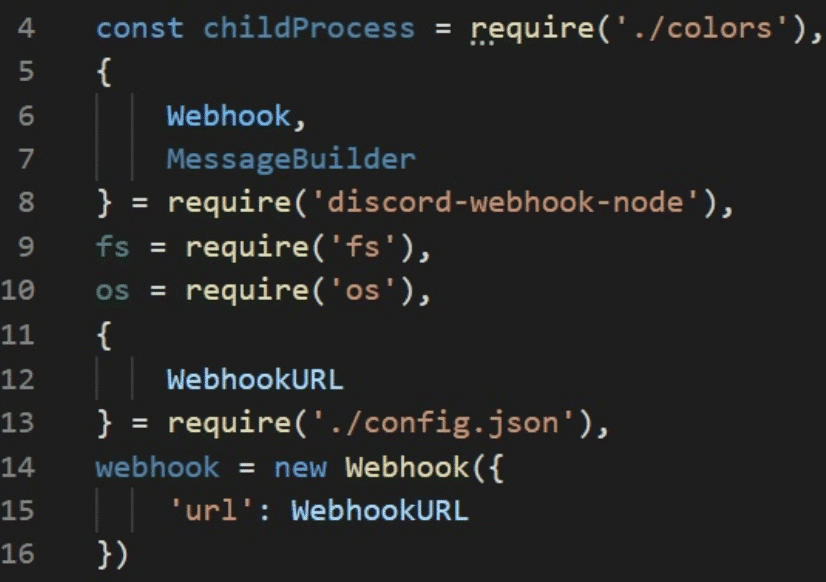
colors-1.0-v-1.4.0 is an obfuscated package that tries to harvest the authentication tokens of common applications such as Discord, Sputnik, Yandex, Chrome, Edge, Opera, and more. In addition, it gathers geolocation, PC information, and Discord user information. It then exfiltrates the information through a webhook to discord-bot.
The following shows some de-obfuscated code sections from the package:
Example 3
Here, another attacker has published five malicious packages that steal some basic information about your system. The packages are iscordjs, Disocrd.js, Discodr.js, Discordj, and Discordks.
Example 4
The package @superbet-group/allowance-js was published on March 31, 2022 and was blocked by Mend Supply Chain Defender just 25 minutes after its creation. The package tries to reverse shell which is a type of session attackers often use to open communication ports between their machines and the victims’ machines.
On March 31, 2022, Mend Supply Chain Defender blocked 56 different malicious packages from NPM registry, which make a total of 493 different versions that were blocked in this batch of 56 different packages alone. The packages vary from collecting user info, typosquatting, reverse shell attacks, and more. The full list is:
| calc_qyjtnetl1b | @8×8/oxygen-constants | @aws-ee/base-services |
| eslint-plugin-coinbase | allowances-js | @superbet-group/web.types |
| vue-loader-3 | web.lib.vue-utilities | @superbet-group/betting.lib.payments |
| frontend-framework-paypal | @superbet-group/web.lib.flags | @superbet-group/allowances-js |
| calc_orffu561zo | @superbet-group/web.lib.utilities | web.types |
| calc_kvhnkm0vxb | web.lib.rest | teststast-js |
| calc_eeh9p9ahuh | @superbet-group/web.lib.logger | @superbet-group/web.lib.rest |
| berakss | @superbet-group/web.lib.config | web.lib.flags |
| @c0rv4x50/c0rv4x4xpackage | web.lib.config | @superbet-group/web.lib.ui-components |
| tw-ui-resources | @superbet-group/betting.lib.validation | @superbet-group/web.lib.vue-utilities |
| testing-npm-random | betting.lib.payments | @superbet-group/martech.lib.google-analytics |
| random-testing-npm | @superbet-group/web.lib.global-styles | data-api.js-core |
| new-random-test | colors-personaly | @superbet-group/allowance-js |
| flow-common | colors-art | savik-poc |
| raygun.status | colors-design | savikpoc |
| sa-383-bulk-creative-update | openzeppelin-solidity-2.3.0 | ardoq-sheet-load |
| my_app_or_test | b0x.js | @bijie/react-bnb-biz |
| global-proxy-agents | @defidollar/core-client-lib | @bijie/react-bnb |
| discord-anti-spam-ban | spr-base-ui |
Bottom Line
The bottom line is that it doesn’t really matter whether the attacker uses automation to launch a large-scale attack or manually publishes just a few malicious packages. This happens, and it will happen again. In fact, this particular case doesn’t even change any aspect of the attack surface.
However, there are still safety measures that need to be taken by package managers—any barrier that helps impede the so-called spamming of package managers is important.
One such measure is CAPTCHA when uploading new packages. Although there are ways to bypass CAPTCHA, having this simple yet important mechanism is the least we can expect from a package manager to have as an extra safety measure.
Organizations and users should inspect and analyze each package they’re importing, in order to prevent dependency confusion or any malicious package from entering their software supply chain attacks. Developers and organizations should also check who maintains the packages they download and choose carefully what to download.
Given the nature of NPM and other big popular package managers, we would expect to see more of these types of attacks in the near future. But we will get used to this, just like we all got used to spam mail, or phishing attacks through email. Of course, the easiest way to protect this attack surface is to use an automated supply chain security solution such as Mend Supply Chain Defender. Doing so helps ensure that even large-scale attacks such as this one are blocked.