Open Source Vulnerabilities Overview: Apache Struts vs. Spring

Table of Contents
Developers the world over depend on the frameworks like Apache Struts and Spring to build valuable and powerful applications.
These massive open source projects have provided organizations with a cost-effective force multiplier that allows their teams to develop faster and more efficiently. In GitHub, Apache Struts is a very active project, having over 6,000 commits and 121 releases. The Spring Framework boasts 22,460 commits and 208 releases.
The Struts and Spring communities work hard to stay on top of security. That means investing in security research to ensure that vulnerabilities are detected, fixed, and published as soon as possible so that users and their customers stay secure.
The Mend.io knowledge team took a deep dive into the data to learn about existing and emerging security trends in Struts and Spring.
The notorious Equifax breach and Apache Struts
Apache Struts made headlines a few years ago with the breach of the US-based credit rating agency Equifax. Despite the warnings from government agencies and the National Vulnerability Database (NVD) that the version of Apache Struts 2 that they were using was extremely vulnerable to remote code execution attacks (CVE-2017-5638), the company failed to remediate the flaw when it was reported.
Even though the Struts team did everything right when CVE-2017-5638 was detected, the software development industry remained on edge. When a year later a new critical Struts vulnerability popped up, many companies braced themselves for the next Equifax-level breach report.
With this baggage associated with Apache Struts history, it is worth checking whether the project deserved the negative attention. In hopes of understanding Struts security profile, we decided to compare it with another popular project, Spring.
Comparing Apache Struts and Spring vulnerabilities
When we look at the number of vulnerabilities published for each project, the numbers are actually relatively low for both projects.
Given the popularity of the projects, it is safe to say that plenty of security researchers are pouring through the code. When you bring together as much code and as supportive a community as we see in projects like Apache Struts and Spring, you are going to detect vulnerabilities. The low volume of issues published shows us that both teams have a good handle on their projects and are putting out secure components.
We also checked the severity breakdown and we found that Spring has more medium vulnerabilities than high and critical ones, while Apache Strut’s severity breakdown is more in line with the severity breakdown for open source vulnerabilities in general. the Struts teams detect and publish more critical and high vulnerabilities than medium ones.
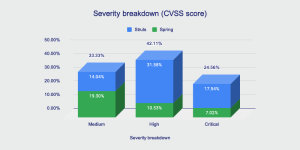
Apache Struts and Spring vulnerabilities: Time to fix
While the number of published vulnerabilities can tell us a lot about a project’s security profile, no less important is how vulnerabilities are handled by the teams when they are detected.
Happily, we found that both the Struts and Spring teams have been doing a great job fixing vulnerabilities once they are confirmed.
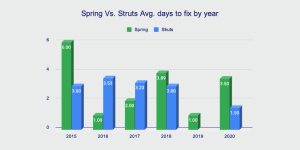
Data shows that over the past few years the Struts project in particular has done excellent work minimizing their time to fix vulnerabilities, achieving a 1.5 day time to fix in 2020. While it takes the Spring team a little longer, the 3.5 day average that they achieved in 2020 is still impressive.
Key takeaways on Apache Struts and Spring security
It is important to remember that even though new published Apache Struts and Spring vulnerabilities are low, there’s a chance that some of the older CVEs for this project are still kicking around in our software products.
We need to remember that hackers love to use published known vulnerabilities to look for new targets, knowing full well that far too many organizations fail to patch even after a fix becomes available.
If you are not using the right tools to keep an updated inventory of what you have, identifying which ones have known vulnerabilities then you could be exposed to a highly preventable attack.
For the users of open source components — which is nearly everyone — the question should not be Apache Struts vs. Spring vulnerabilities, but how do we manage them?


