Best Practices of Highly Effective AppSec Programs

Table of Contents
As the pace of application development accelerates, many companies face a growing challenge: how to reinforce security while keeping pace with the schedule of releases. New research from TechTarget’s Enterprise Strategy Group (ESG), commissioned by Mend.io, shows that only 52 percent of companies said they can effectively remediate a critical vulnerability, even though 69 percent have directly encountered at least one serious security incident from a software vulnerability over the last twelve months.
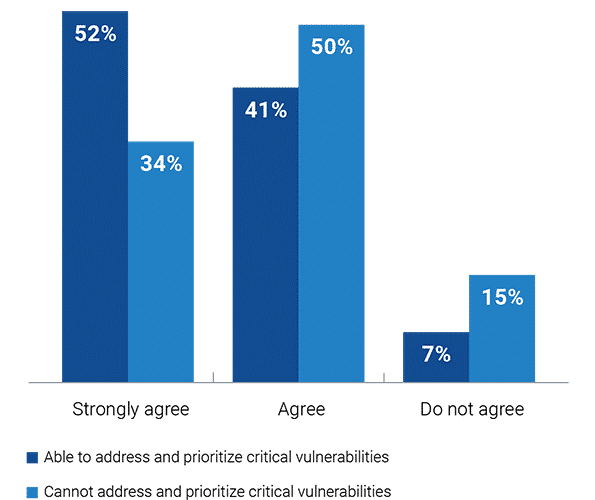
As it turns out, the 52 percent of respondents that can keep up with vulnerability remediation tend to outperform those that can’t in several important areas, and it pays off. These companies were nearly twice as likely to say they have not experienced any serious security incidents tied to a software vulnerability/web application exploit over the last 12 months.
So what are some important differentiators? Let’s take a look:
Know what’s in your code. Better visibility into their code base gives companies better control over it. Organizations that report the ability to efficiently remediate vulnerabilities were much more likely to say they view being able to answer questions about their code as critical, including being able to document the composition of their code, assess where their code is stored, know their code’s provenance, and who has access to code components.
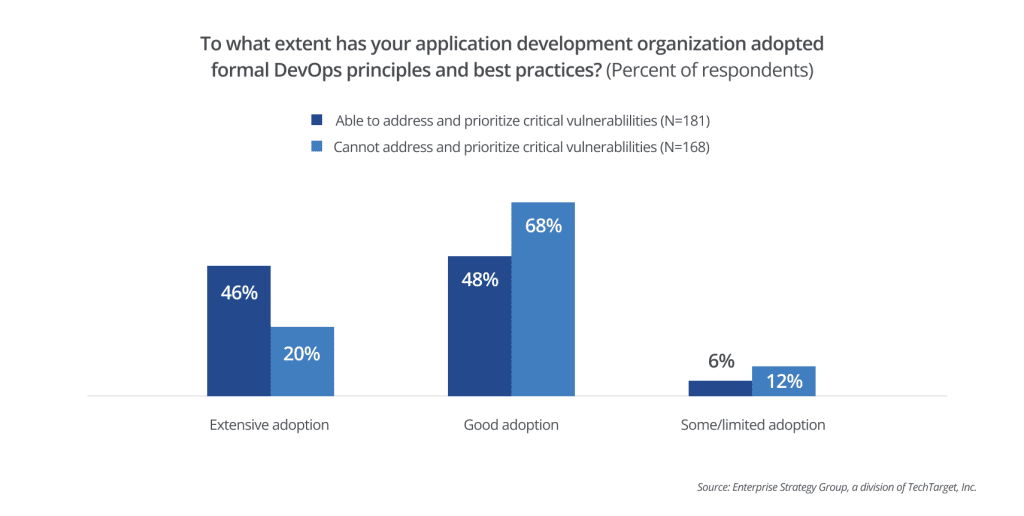
Embrace DevOps. The speed and volume of development means that the responsibility for security must now extend beyond just security teams. Security is increasingly shifting left, earlier in the software development lifecycle (SDLC), so it benefits from the involvement of development teams in a DevOps approach that incorporates security processes into development. Organizations that report the ability to efficiently remediate vulnerabilities were more than twice as likely to report they have extensively embraced DevOps.
Drive collaboration to build a culture of security. The overwhelming majority of companies with effective remediation programs — 93 percent — say that they encourage collaboration between application development, security, and operations to build a culture of security. With this culture in place, developers are more likely to willingly implement secure coding practices and work regularly with others to help protect their codebase. Organizations that promulgate shared responsibility create trust between developers and security and succeed in building stronger, more secure AppSec processes.
Indeed, the earlier the better. Organizations that initiated collaboration during the “requirements and design” phase of the SDLC exhibited a lower average of 2.3 serious security incidents compared to 3.2 incidents experienced by organizations that engaged in collaboration only during the SDLC’s later stages. This highlights how effective early-stage teamwork can be in strengthening security, staying ahead of threats, and minimizing vulnerability-related risks.
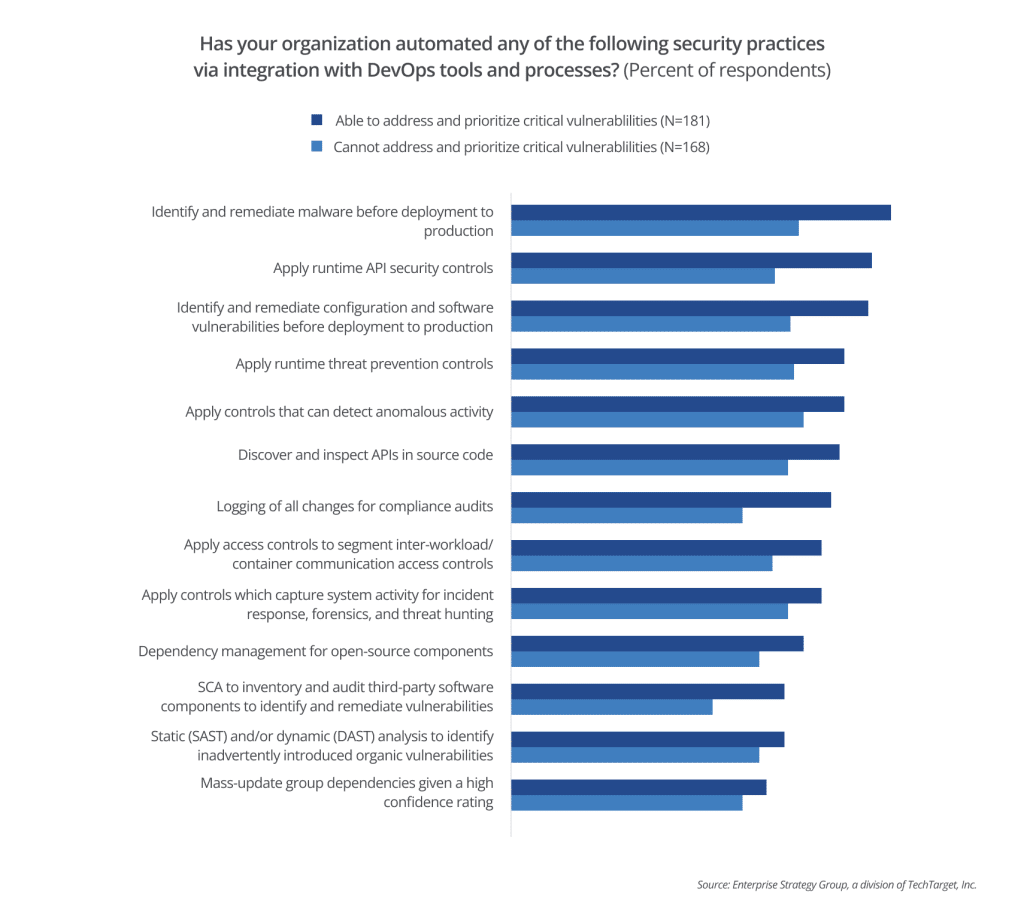
Deploy automated tools. Effective application security programs embrace automation. According to the report, organizations that can keep up with critical vulnerability remediation more often automate the identification and remediation of malware (83 percent) and configuration and software vulnerabilities before deployment to production (78 percent). It encourages developers to adopt best security practices by making security a seamless part of their workflow that’s easy to implement and adopt. Automation overcomes developers’ objections that security processes hinder them and drives the collaboration that’s so valuable for hardening security.
What tools give you great AppSec?
Hardening your AppSec involves a combination of tools to comprehensively identify, update, and fix flaws, vulnerabilities, and threats to your code base. The most prominent are:
SBOMs. The research highlights the need to address third-party and open source software (OSS) because developers use vast libraries of this software to build their applications. Visibility is essential to achieving this. We’ve already noted the importance of understanding the provenance of code and where it’s stored. Organizations that do this well are much more likely to say that generating a software bill of materials (SBOM) is a mandatory part of their application development process.
SCA. Organizations that are confident about their security identify and remediate malware and vulnerabilities earlier in the SDLC. Nearly two-thirds of them (60 percent) use software composition analysis (SCA) to achieve this with OSS. SBOM inventory and audit capabilities are also key to addressing important issues of open source compliance. 70 percent of organizations confident in addressing and prioritizing critical vulnerabilities say they log all changes in software for compliance audits.
Dependency management enhances the job that SCA does for OSS by ensuring that the dependencies you’re using in OSS are updated so that vulnerabilities can’t impact your codebase. Automated dependency management makes this even more efficient. Unsurprisingly, 64% of organizations confident about their security implement dependency management.
SAST. Alongside these tools, 60 percent of these organizations are using static application security testing (SAST) or dynamic testing (DAST) to scan their proprietary code and identify and fix vulnerabilities.