Learn about our innovative approach to detecting and remediating custom code vulnerabilities for a more secure future.


Learn about our innovative approach to detecting and remediating custom code vulnerabilities for a more secure future.

Discover how DevSecOps integrates with Agile to enhance security and speed in software development. Learn best practices & more.

Learn about Infrastructure as Code (IaC) and its benefits for DevOps success. Discover best practices for secure use and tools.

Discover why adopting Zero Trust security is essential for DevSecOps in the ever-evolving world of digital assets.

Learn how to transition from DevOps to DevSecOps with our step-by-step guide. Discover the benefits, challenges, and best practices.

Learn how to secure your package manager’s lockfiles to protect your application from supply chain risks and ensure version consistency.
Discover the differences between DevOps and Agile methodologies in software development. Learn how they can be combined.

Discover the 9 best DevSecOps tools to integrate into your DevOps pipeline. Learn how these tools can help you automate security, & more.
A detailed comparison of Docker vs. Kubernetes, explaining their differences and similarities. Learn how they complement each other.
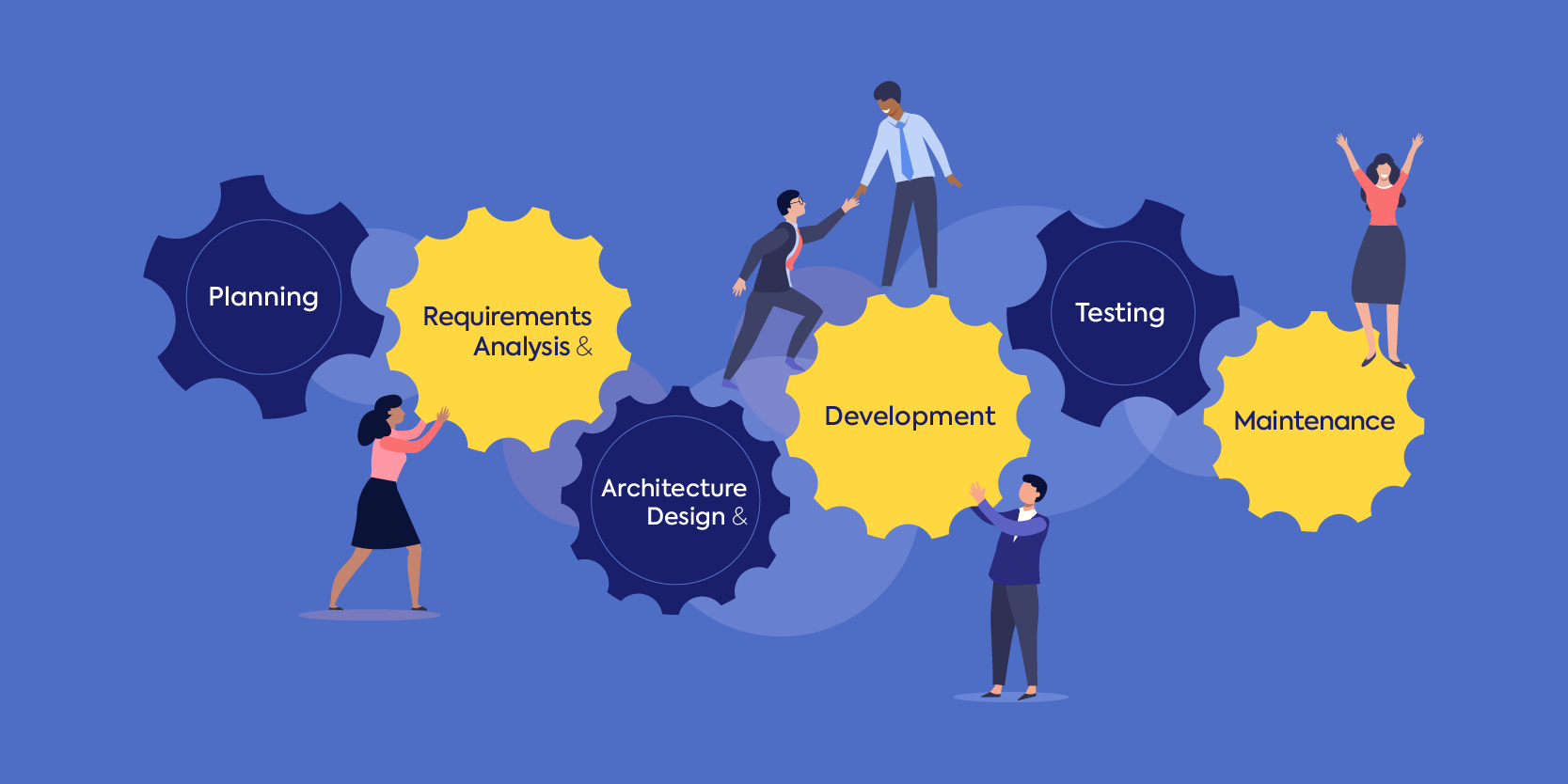
Learn how to secure your software development life cycle (SDLC). Discover the importance of integrating security throughout the SDLC.

Discover how developer security champions play a crucial role in the DevSecOps revolution, promoting secure coding best practices.

Learn when to consider using a NoSQL vs relational database in your org. Understand the benefits & where NoSQL may be the better option.
Learn about Docker containers and whether your company should adopt them. Discover the benefits, challenges, and security considerations.
Learn about microservices architecture and the security strategies and best practices needed to protect your organization’s systems.

Discover the top 10 open source vulnerabilities in 2020, including Lodash, Jackson-databind, HtmlUnit, and more.

Learn about the main features of Eclipse SW360, an open source tool to manage software components.