The new Chinese owner tampers with the code of cdn.polyfill.io to inject malware targeting mobile devices.
The new Chinese owner tampers with the code of cdn.polyfill.io to inject malware targeting mobile devices.
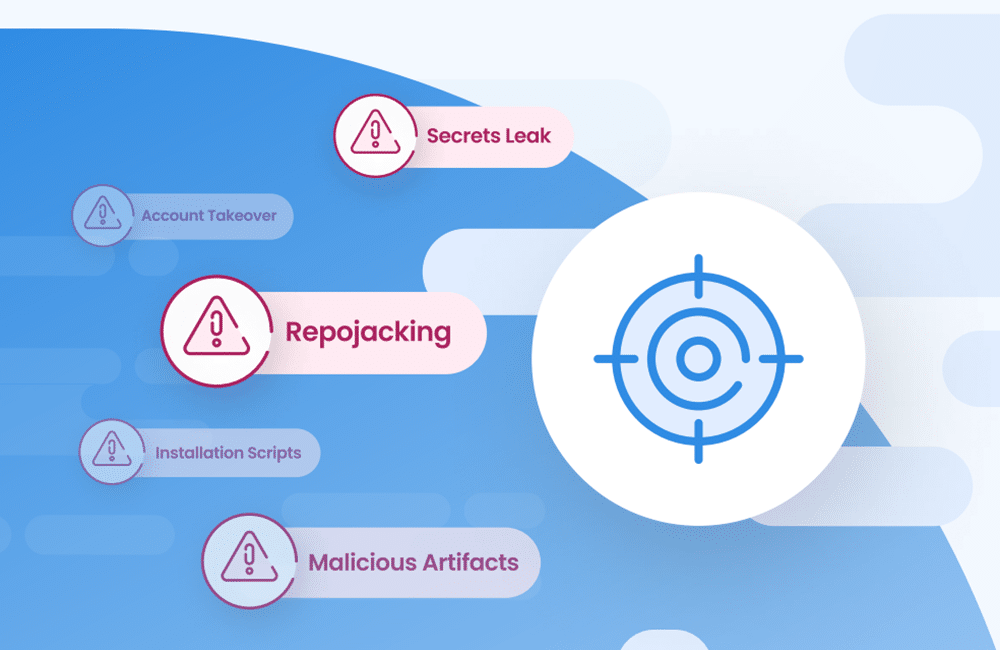
Learn more about supply chain threats and where to find them.
Discover how CVE-2024-3094 affects XZ Utils and enables SSH compromise. Get insights on detection, mitigation, and system security.
Discover the top tools for automating SBOMs on our blog. Learn how to create SBOMs effortlessly and boost your supply chain security.

Learn how to strengthen your security posture with holistic approaches to application security and software supply chain security.

Discover six top tips for holistic application security and software supply chain security for long-term success.

Discover effective strategies for handling security team turnover, maintaining tool efficiency, and fostering strong developer relationships.
Explore the security threats arising from the boom in AI and LLMs, including data privacy, misinformation, and resource exhaustion.

Learn why it’s important to let software products die gracefully rather than become zombies, affecting security and functionality over time.

New ESG Research Report reveals best practices for application security programs. Learn how to prevent incidents and secure software apps.

Discover why the US government is prioritizing software supply chain security. Learn about CISA’s goals and objectives at the SOSS Summit.
To mark Cybersecurity Awareness Month 2023, discover five key reasons why automated software updates are so vital for your application security.
Discover the importance of dependency management in securing the software supply chain as regulations escalate.

Discover the importance of automation in cybersecurity and how software vendors can stay ahead of adversaries.
Learn how to effectively communicate the value of your company with Software Bill of Materials (SBOMs).
Learn about software supply chain security basics and best practices to prevent attacks.