Critical Backdoor Found in XZ Utils (CVE-2024-3094) Enables SSH Compromise 1
Table of Contents
On March 29th, 2024, a critical CVE was issued for the XZ-Utils library. This vulnerability allows an attacker to run arbitrary code remotely on affected systems. Due to its immediate impact and wide scope, the vulnerability has scored 10 for both CVSS 3.1 and CVSS 4, which is the highest score available.
In this article, you’ll learn how this backdoor infiltrated the software, the potential consequences of an attack, and how to identify and patch vulnerable systems.
This article is part of a series of articles about malicious packages.
What is XZ-Utils?
XZ-Utils is a collection of tools for the XZ compression format that have high compression ratios and fast decompression. The XZ format utilizes the LZMA2 compression algorithm, an improved version of LZMA that provides better compression and improved flexibility in the compression process. The XZ-Utils package typically includes several command-line tools for compressing and decompressing files. One of the most commonly used is XZ itself.
What happened
On Friday, March 29th, a developer named Andres Freund issued a security advisory regarding a backdoor he found in the upstream XZ/liblzma 5.6.0 and 5.6.1 versions that led to SSH server compromise. After he noticed some odd symptoms around liblzma, such as SSH login taking up too much CPU, and debugging with valgrind, he figured out that the XZ tarballs have been backdoored.
Backdoor mechanism
The backdoor was not directly inserted into the source code of liblzma that is visible in version control systems or utilized by XZ directly. Instead, it was hidden within binary test files in the XZ compressed format. These files appeared benign and were theoretically part of the library’s test suite.
The attackers used a sophisticated method that split the backdoor into parts, which were then concealed within two XZ compressed files. These files were disguised as ordinary test files, evading detection from casual inspection or automated tools that scan for malicious patterns.
Those crafted test files can be found here:
tests/files/bad-3-corrupt_lzma2.xz (cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0, 74b138d2a6529f2c07729d7c77b1725a8e8b16f1)
tests/files/good-large_compressed.lzma (cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0, 74b138d2a6529f2c07729d7c77b1725a8e8b16f1)
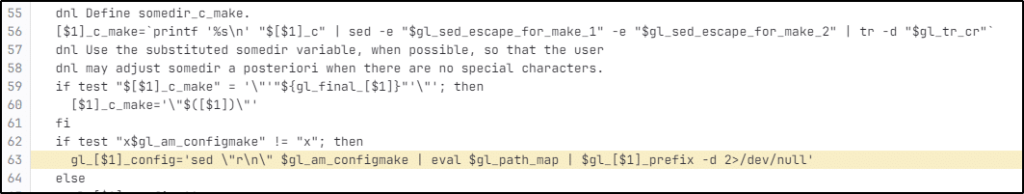
Figure 1. Different version of build-to-host.m4 file in the released tarballs
Execution flow
Upon decompression and execution, these files collaboratively manipulated the build process of liblzma. The process involved extracting and executing obfuscated script code, leading to the injection of malicious code into the build output.
This manipulation effectively appended malicious data to the build process without raising suspicion, as it mimicked legitimate testing adjustments.
The deobfuscated code can be found here
Malicious code injection
The attackers introduced a new object related to the CRC64 algorithm, claiming it was an improvement. This object was, in fact, a trojan that, when included in the build process, embedded the final backdoor into the liblzma library.
The essence of the backdoor was to intercept function calls related to CRC32 and CRC64 resolution and replace them with malicious variants that could execute arbitrary code under certain conditions, likely tied to specific crafted inputs.
Linker manipulation and RSA decryption hook
The backdoor installed an “audit hook” into the dynamic linker of Linux, a critical component that resolves library dependencies at runtime. By hooking into this mechanism, the backdoor could alter the behavior of the linker to intercept and modify the resolution of symbols, particularly those involved in RSA public key decryption.
This manipulation meant that during SSH key authentication, the backdoor could substitute the legitimate RSA decryption function with its own, allowing for unauthorized access if the input matched a certain condition likely known only to the attacker.
Stealth and implications
The backdoor’s sophistication lay in its ability to hide within the normal build process and manipulate low-level system components undetected. Targeting the dynamic linker and encryption routines posed a severe threat to system security, potentially allowing attackers to bypass authentication mechanisms.
How to look for the XZ package with Mend Container
With the Mend Container solution, you can effortlessly scan individual images or integrate your container registry to scan your entire registry thoroughly. Additionally, you can leverage our in-house container reachability analysis to check if the vulnerability is reachable. Our updated scanner will enhance your knowledge with the most updated data regarding this vulnerability.
Vulnerable Linux distros and their fix versions
| Distro | Distro Versions | Is Affected? | Fixed Versions | References |
| Alpine | edge | Affected | 5.6.0-r2, 5.6.1-r2 | alpinelinux.org |
| Debian | Unstable (sid, trixie) | Debian stable versions are not affected | 5.6.1+really5.4.5-1 | security-tracker.debian.org |
| Ubuntu | – | Not Affected | – | ubuntu.com |
| RHEL | – | Not Affected | – | access.redhat.com |
| Fedora | 40 | Not Affected | 5.4.6-3.eln136 | fedoraproject.org |
| Fedora | 41 | Affected | – | fedoraproject.org |
| Fedora | Rawhide | Affected | – | fedoraproject.org |
| Amazon Linux | – | Not Affected | – | aws.amazon.com |
| OpenSUSE | Tumbleweed | Affected | 5.6.1.revertto5.4 | news.opensuse.org |
| Arch Linux | – | Affected | 5.6.1-2 | archlinux.org |
False positive announcement
Due to a conflict between the Debian advisory and the official announcement, customers are expected to detect false positive alerts on older versions than 5.6.0. We recommend either upgrading to the matched fixed version listed above or downgrading to the latest uncompromised version, which is 5.4.6.
*April 1 update. It was confirmed that Fedora 40 is not affected by the backdoor. However, users should still downgrade to a 5.4 build to be safe.
A landscape of malicious packages
The critical backdoor found in XZ Utils serves as a stark reminder of the evolving threats within the software supply chain. While this specific vulnerability involved a backdoored library, malicious actors employ various techniques like license tampering, credential theft and many more.
In conclusion, the XZ Utils backdoor vulnerability (CVE-2024-3094) underscores the critical need for vigilance in software supply chain security. By staying informed about these evolving threats, implementing robust security practices, and patching vulnerable systems promptly, organizations can significantly reduce their risk of falling victim to malicious attacks.



