How Software Supply Chain Attacks Work, and How to Assess Your Software Supply Chain Security

Table of Contents
When it comes to applications and software, the key word is ‘more.’ Driven by the needs of a digital economy, businesses depend more and more on applications for everything from simplifying business operations to creating innovative new revenue opportunities. Cloud-native application development adds even more fuel to the fire. However, that word works both ways: Those applications are often more complex and use open-source code that contains more vulnerabilities than ever before. Then too, threat actors are creating and using more attack methods and techniques, often in combination.
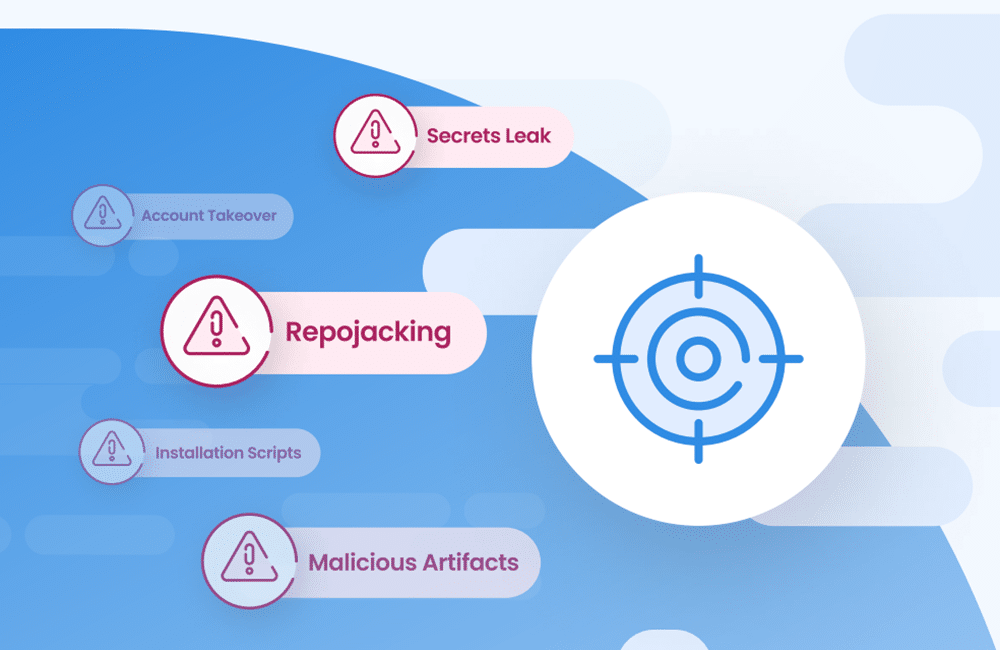
Ultimately, we end up with a smorgasbord of attack opportunities, and threat actors know it. In fact, Mend.io’s recent report on software supply chain malware saw a 315 percent jump in the number of malicious packages published to npm and rubygems from 2021 to 2022. These attacks often compromise trusted suppliers or vendors. And precisely because they exploit trusted relationships, they can be quite difficult to detect and repulse.
So how can you defend against them? Here are a few ideas.
How do software supply chain attacks work?
The software supply chain is the network of suppliers and vendors that provide the software components for applications. Adversaries compromise third-party software to gain access to your systems and code base. Then they move laterally through your supply chain until they reach their intended target.
Generally, software supply chain attacks follow a series of stages.
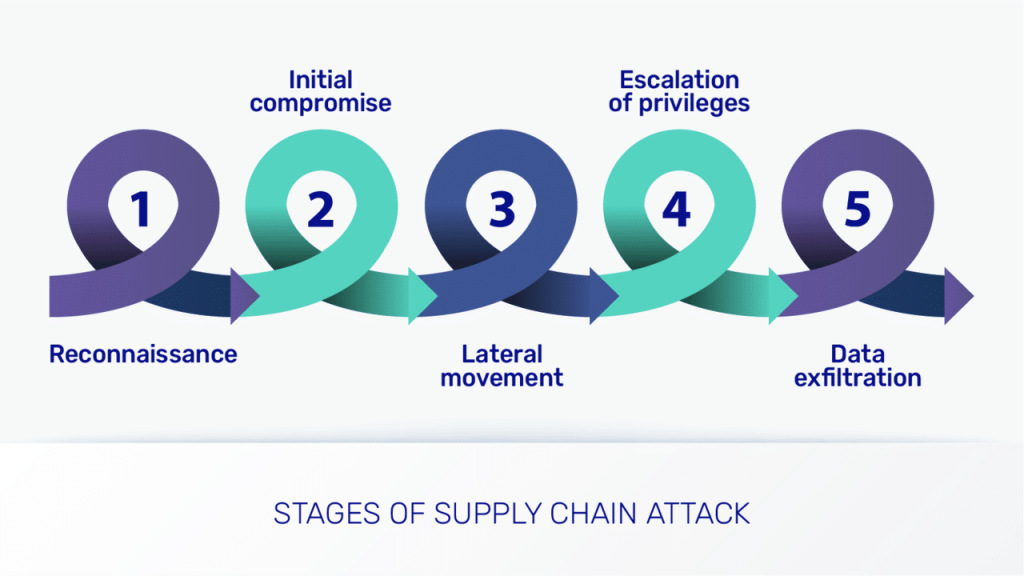
- Reconnaissance. Malicious actors research their target and identify vulnerabilities in the supply chain. This involves gathering information on the suppliers, vendors, and partners within the supply chain.
- Initial compromise. The first access to a vulnerable point in the supply chain, like a third-party supplier or vendor. It may involve phishing and other social engineering to trick employees into providing access credentials.
- Lateral movement. Once inside the supply chain, attackers try to gain access to other systems or data, using things like stolen credentials or exploit vulnerabilities.
- Escalation of privileges. Attackers seek to gain administrative access to critical systems within the target enterprise, like domain controllers or other servers that hold sensitive data.
- Data exfiltration. Data or intellectual property is stolen, or other disruption is caused.
By understanding these stages, you can take steps to detect, mitigate, and prevent software supply chain attacks before they cause significant damage.
Common vulnerabilities
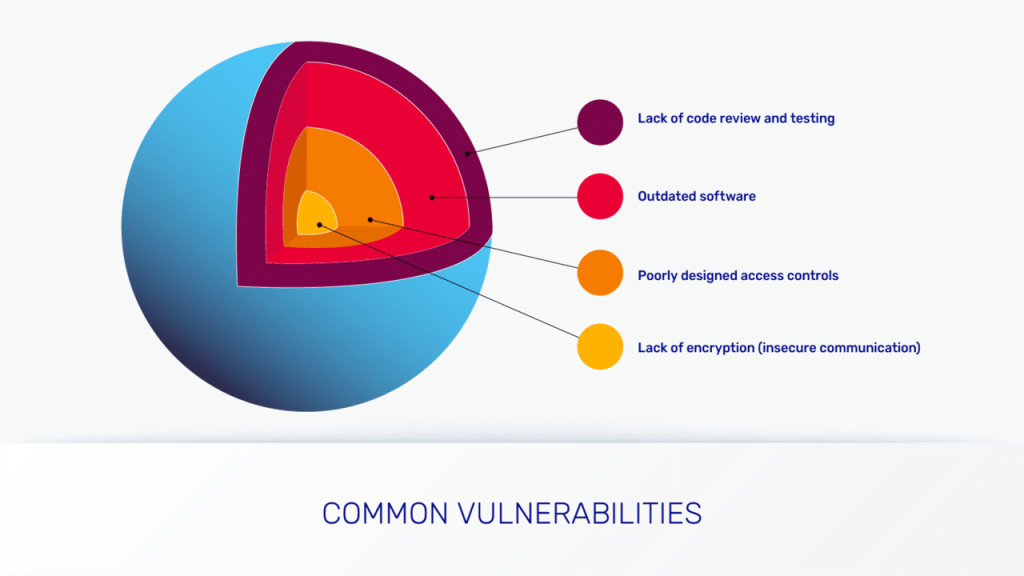
Software supply chain security weakness can most often be caused by:
- Insufficient code review and testing, resulting in vulnerabilities going undetected. Enterprises should implement a comprehensive code review and testing process to identify and mitigate any potential security issues.
- Outdated/unpatched software leaves systems vulnerable to known security vulnerabilities that attackers exploit.
- Poorly designed access controls and weak authentication allow attackers to easily gain unauthorized access to sensitive systems and data.
- Weak encryption and insecure communication make it easy to perform data breaches.
If an enterprise doesn’t have the tools or expertise to effectively monitor and detect threats, the lack of visibility into the supply chain increases the risk of exposure to potential issues. That’s the first of some hidden vulnerabilities that also pose a threat. The others are:
Hidden vulnerabilities

- Third-party dependencies. Applications often rely on third-party libraries and components, which can introduce vulnerabilities if they are not properly managed. These can be difficult to detect, especially if the enterprise has poor visibility into the source code.
- Lack of diversity in software suppliers. If an enterprise relies on a single software supplier and doesn’t have visibility into its security practices, then it can’t effectively detect hidden vulnerabilities.
- Attacks targeting open-source software happen because enterprises use open-source so heavily that it’s an enormous attack surface.
How do you assess your supply chain security?
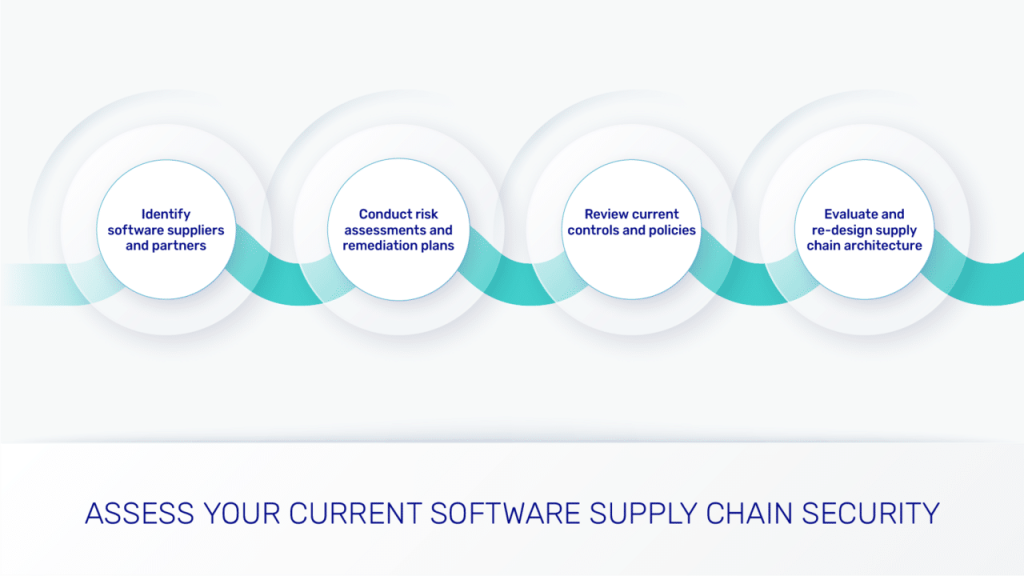
- Identify software suppliers and partners. Generate a software bill of materials (SBOM) — an inventory of all your vendors, contractors, and other partners, checking their security policies and controls, and their compliance with regulations.
- Conduct a risk assessment and set up remediation plans, including robust software testing and enhancing security awareness.
- Review and implement your controls and policies. Ensure your policies meet security requirements. Check access control and data protection to prevent unauthorized access, strengthen confidentiality, limit the attack surface, and mitigate third-party risks.
- Practice encryption and secure communication
- Evaluate and redesign supply chain architecture, to increase supply chain visibility, better identify and manage potential issues, malicious activity, third-party risks, and ensure you meet compliance and regulatory requirements.
Tools to strengthen security
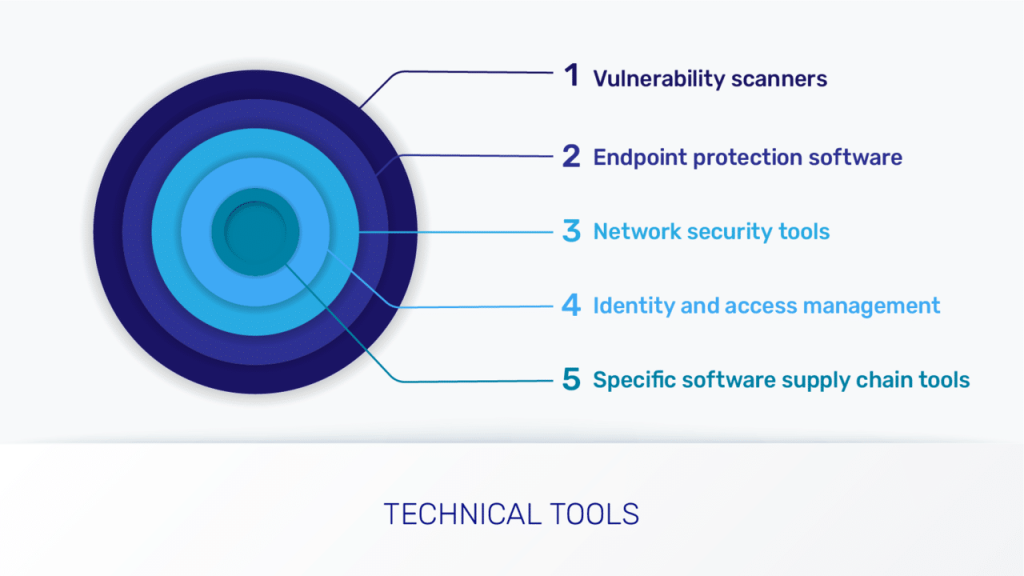
Build a holistic approach to security. Use a combination of vulnerability scanners, endpoint protection software, network security tools, identity and access management, and specific software supply chain tools, alongside employee training and response planning.
In my next blog post, I look at how you do this successfully, and what you should do with these tools to harden the security of your software and applications.