MiFID II Reforms and Their Impact on Technology and Security

Table of Contents
In the latest round of regulations for companies doing business in the European Union, MiFID II will require some important overhauls for how data is stored.
The European Union’s recent set of reforms known as the Markets in Financial Instruments Directive II (MiFID II) will have a huge impact on the entire financial industry, covering big banks, asset management companies, and wealth managers. MiFID II, which is the overhauled version of MiFID I, presents many new challenges for these organizations in terms of investments, trades, etc. These reforms take into account the tough lessons from the 2008 financial crisis and the developments that have taken place in the trading environment since MiFID I was put in place.
The MiFID I reforms were predominantly focused on reporting about equities and bonds, but with MiFID II, the scope of reporting has expanded to include commodities, currencies, and credit products. With this greater volume of transactions that need to be reported under MiFID II, storage and IT infrastructure requirements will increase exponentially, as will data security and integrity needs.
This has left many wondering what the MiFID II technology impact will be as they plan for the year ahead.
Whether it is stored on-premises or in the cloud, your data is your organization’s most prized possession, which many malicious actors will try to access and exploit. Therefore, the cyber security wing of your organization has lot of work to do to make sure that your business and reputation remain intact.
In this post, we review the basics about the MiFID II reforms and the impact they will have on your organization’s IT and security. We also offer a few strategies and suggestions on how to handle these new challenges.
How is MiFID II Different from MiFID I?
So, what sets MiFID II apart from MiFID I? MiFID II provides for increased market transparency and investor protection, technological innovations, better governance, and a level playing field for all participants. The diagram below has more details about MiFID II’s objectives.
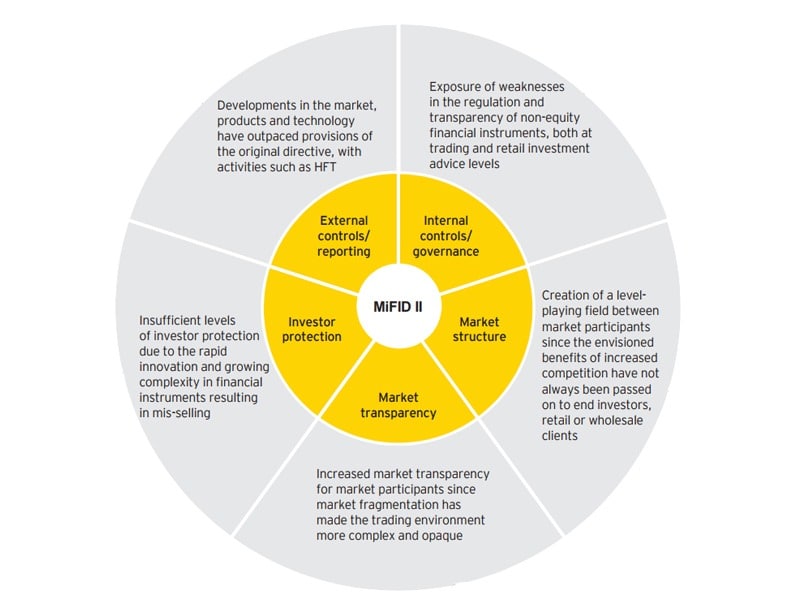
Image 1: Core objectives of MiFID II
Image credit: EY
One of the most significant changes is the wider scope of reporting that is required under MiFID II. For example, now you are obligated to report a much larger number of fields per transaction than you had to with MiFID I. Basically, anything that is traded on a multilateral trading facility (MTF) must now be reported.
Please note that the January 3, 2018 go-live date for MiFID II has already passed, so if your organization is not in compliance with the new rules yet, we urge you to make this a priority.
The penalties imposed for MiFID I violations were already very steep, and it is safe to assume they have become even harsher under MiFID II. Twelve companies were fined under MiFID I, including Merrill Lynch International. To give you an idea of how serious the consequences were, Merrill Lynch was slapped with a whopping 13,285,900 GBP fine. As of now, we do not know what the fine will be for a similar offense under MiFID II, but we know that it will be worse. The increased severity of fines, combined with the many additional instruments that have come under the purview of reporting under MiFID II, will put much greater pressure on organizations than MiFID I did.
A single breach is enough to stall your business and cause financial losses in the form of huge penalties. Considering these significant consequences, avoiding breaches is more important for your organization’s survival than ever. Your cybersecurity teams will inevitably bear much of this burden. So, which technology and security changes will need to be implemented to improve your security and steer clear of MiFID II violations?
MiFID II’s Impact on Technology
MiFID II requirements are primarily compliance-oriented, but technological innovations play an equally important role in meeting the new requirements. MiFID II will affect multiple areas in technology, including:
- Data storage, aggregation, and analytical requirements: Under MiFID II rules, all of the records that can impact or lead to a trade must be retained for posterity. This includes records pertaining to phone calls and emails. Managing this volume, variety, and velocity of data (i.e., big data and extracting numerous mandatory reports) will be a herculean task. A complete data retention and archiving strategy also needs to be designed. This might require a huge amount of storage not only at your primary data center, but also at your disaster recovery site, which can be taxing in terms of costs and implementation.
- Integration between disparate applications: MiFID II will force integration of various applications with trade platforms to provide some of the key inputs. For example, your insurance portal might need to communicate with the trade system to feed the national insurance number in order to complete the transaction. There are multiple ways to carry out integrations like these, but application programming interface-based (API-based) integration is most efficient and robust in most cases.
- Enhanced and transparent client portal: To adhere to investor protections, organizations need to build proper client classification and client data inventories. This will be very useful for client-facing and for sales representatives to offer the appropriate products and services to the right customers. Institutions can also look forward to providing clients with real-time access to account information through these portals. Technology will once again play a key role in the development and enhancement of required portals and dashboards.
- Mobile Device Management (MDM) strategy: As mentioned above, the new set of rules mandates that you record and store all trade-related phone calls. As per the directive of the European parliament, “[f]or those purposes, an investment firm shall take all reasonable steps to record relevant telephone conversations and electronic communications, made with, sent from or received by equipment provided by the investment firm to an employee or contractor or the use of which by an employee or contractor has been accepted or permitted by the investment firm.” So, what if the communication is happening over social media like Facebook or WhatsApp? It is impossible to record these discussions as they are encrypted. The solution is to roll out an MDM product, which restricts individuals from installing these sets of applications, thus compelling them to use modes of communication that will allow for compliance.
Cyber Security Requirements
We must also consider the IT security requirements that come along with MiFID II. In addition to the collection and retention of enormous amounts of data, maintaining the security and integrity of that data is a major challenge.
Data security requires an access management system, which ensures that only a certain group of individuals has the specific set of privileges to access data. Multi-factor authentication should also be considered to protect your valuable data. Data integrity involves maintaining the consistency and accuracy of data until its life cycle is complete.
Data will obviously be modified over time, but a proper monitoring and auditing system should be implemented to record the identities of individuals, the data and time of entries, modifications, and deletions. Having a robust backup and recovery solution in case an unexpected event occurs is key to restoring normalcy to the organization. This should also be followed up by frequent, internal audits to make sure that all controls and processes are being followed.
Using MiFID II as a Long-Term Strategy
These new reforms might seem like an annoyance, but if your organization chooses to embrace them, the rewards can be great. If your information technology department follows a strategic approach, MiFID II reforms can be a golden opportunity. First, the reforms present an opportunity to reduce the operational expenses. With digitization of workflows and automation of manual, repetitive activities, operational costs can be reduced.
MiFID II also gives your organization the chance to overhaul its legacy applications. You can plan and redesign legacy applications using the next five to seven years as a target. With newly designed, robust architecture and the latest technological advancements, your organization can gain a competitive edge over competitors.
In addition, you can use MiFID II to build a robust and scalable storage infrastructure. Predicting the amount of storage that will be needed for the next two to three years is difficult. Storage infrastructure should be designed so that it is scalable and able to meet requirements without major changes to the overall storage architecture.
Using the Cloud as a Solution for Data Storage and Protection
With no up-front investments, zero maintenance fees, or obscurity in terms of data storage sizing, the public cloud is a great option for data storage requirements. In general, cloud implementations are faster than on-premises ones, and they provide the option to automatically scale resources up or down. According to the European Securities Markets Association (ESMA), “[r]ecords shall be stored in a durable medium, which allows them to be replayed or copied and must be retained in a format that does not allow the original record to be altered or deleted.” This proposition strengthens the argument for using the cloud since setting up data center-equivalent disaster recovery for all email and voice recording data is expensive.
Companies like Amazon Web Services (AWS) and Microsoft Azure also provide high durability and availability with their large, global presence. For example, Amazon S3 is designed for 99.999999999% durability and can survive even after the concurrent loss of data in two facilities. Since the cloud allows you to store data in the facility and region of your choice, regulatory and compliance concerns can be taken care of easily. This advantage will lead to better protection of your critical data that is stored in the public cloud (e.g., call recordings and emails).
Conclusion
MiFID II is already making waves with its complicated and sweeping reforms. The reforms will likely force businesses to realign their strategies and rebuild their technology, including cybersecurity. It is important to ensure that your data is not compromised; neglecting to do so can lead to a damaged reputation and can open up lawsuits against your organization.
However, if you choose to embark on the MiFID II journey with a positive attitude, you can unleash hidden opportunities to redesign your storage infrastructure, leverage the public cloud as a quick and reliable disaster recovery solution, re-strategize your data management and analytics, and much more. If your organization takes this bull by the horns, you will be better prepared to deal with tomorrow’s challenges, and you will have a valuable advantage over your competitors.





