
Learn about malicious packages, how they work, and the growing threat they pose to software supply chains.
Read MoreDiscover the importance of Software Bill of Materials (SBOM) and compare the three main formats – SPDX, CycloneDX, and SWID.
Read More
RSA 2023 takeaways, including sessions on supply chain security, translating security for the board, & the psychology of DevSecOps.
Read More
What do Australia’s cybersecurity plans teach us all about the need for advanced application security?
Read More
Enhance your AppSec by integrating with Jira. Learn how Mend’s new Jira Security integration can streamline your security processes.
Read More
Mend.io achieves AWS Security Competency status, demonstrating expertise in cloud security. Trusted partner with specialized software for AWS
Read More
Learn how poor application security can have deadly consequences in the healthcare sector. Discover the new FDA guidance and tools.
Read More
Learn why the need for application security grows as the EU tightens cybersecurity requirements. Understand the impact on organizations.
Read More
Learn why scanning applications in the repository is crucial for application security. Shift left to detect and fix vulnerabilities.
Read More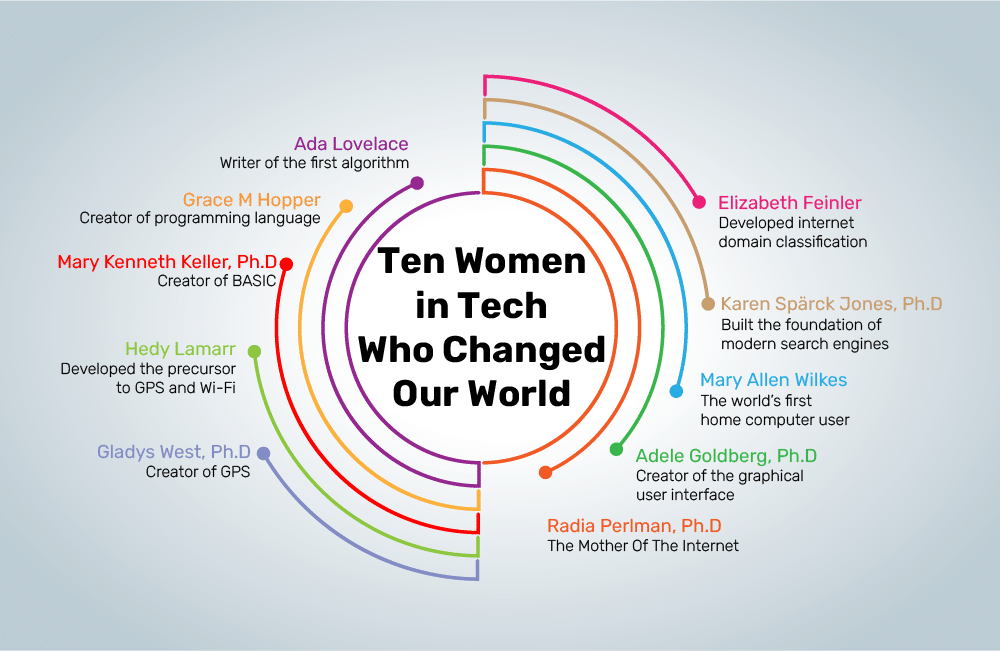
Discover ten pioneering women in tech who changed the world. Learn about their visionary work and revolutionary outcomes.
Read More
Learn about the implications of shifting applications to the cloud on application security. Understand the shared responsibility.
Read More
Learn how the Fintech sector can tackle vulnerabilities like Spring4Shell with speed and efficiency using the Mend platform.
Read More
Discover the key principles of modern application security. Learn how to secure your software and protect against evolving threats.
Read MoreLearn about Kubernetes Security Best Practices, a crucial aspect of managing containerized workflows at scale.
Read More
Discover how Mend’s talented women in tech are leading the way in application security and community. Insights, advice, and career highlights.
Read MoreJoin our subscriber list to get the latest news and updates
Thanks for signing up!
