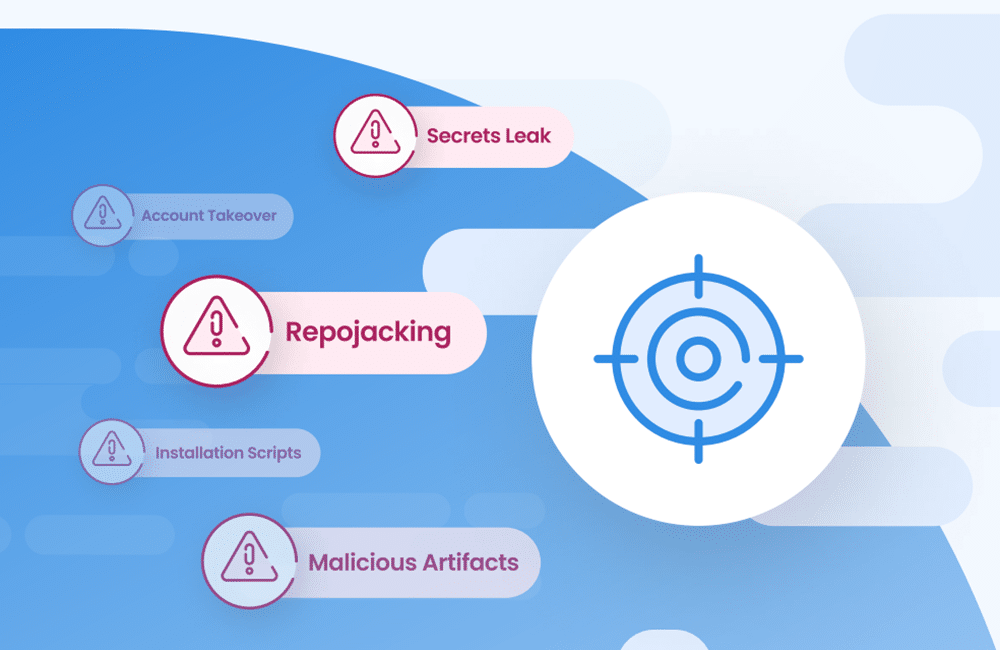
Software Supply Chain Compliance: Ensuring Security and Trust in Your Software and Applications
Table of Contents
Software and applications make the world go round. This naturally makes them a top attack target for threat actors, and highlights the importance of robust software supply chain compliance. But how do companies build and implement a compliance strategy that solves the challenges of modern application security? Let’s take a look.
What is software supply chain compliance?
Software supply chain compliance encompasses a set of practices that organizations adopt to ensure the security, reliability, and integrity of software products and components. By ensuring software supply chain compliance, organizations can reduce the risk of vulnerabilities, protect intellectual property, avoid complex and costly legal and production issues, and maintain the trust of their stakeholders.
What is the scope of software supply chain compliance?
Compliance must extend throughout the entire software supply chain, including development, distribution, and maintenance. Industries that handle sensitive data and processes, such as finance, healthcare, and government, and companies involved in M&A activity, are already subject to strict regulation, and software supply chain compliance forms part of this. However, the increasing connectivity of all organizations means that software supply chain compliance has grown in importance.
Why is software supply chain compliance necessary?
There are four key reasons to implement strong software supply chain compliance strategies:
- The expanding use of software in the production and delivery of services and products More software means more code, components, and dependencies. This means a larger attack surface, and growing potential for flaws and vulnerabilities to create weaknesses in your software supply chain.
- The escalation of highly sophisticated, large-scale attacks on software supply chains. Compromises in the software supply chain can trigger significant consequences, including financial losses, reputational damage, legal liabilities, and data leaks. The SolarWinds attack is estimated to have infected more than 18,000 customers and multiple U.S. government departments, causing billions of dollars of damage. The Log4Shell software vulnerability hit major companies like Amazon Web Services, Cloudflare, iCloud, and more. Jen Easterly, director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), described the exploit as “one of the most serious I’ve seen in my entire career, if not the most serious.” These high-profile attacks are merely the tip of the iceberg. Attacks on vulnerabilities in open source repositories like npm have escalated, and the publication of malicious packages has risen by 315 percent since 2022.
- The implications of breaching the terms and conditions of open- source software components and dependencies. Between 80 and 90 percent of some organizations’ code base now include open source code — and every component and dependency should comply with usage terms and conditions. Companies that fail to comply with these conditions could be forced to remove or re-write code, thereby impeding the production pipeline, disrupting product delivery, and affecting the bottom line.
- Government intervention in the form of new cybersecurity strategies and regulations. In the U.S., the White House cybersecurity strategy has spearheaded the nation’s efforts. This has been reinforced by The National Institute of Standards and Technology (NIST) guidelines for secure software development and supply chain security. They have been complemented by recommendations from the likes of the U.S. Securities and Exchange Commission (SEC), and the Federal Trade Commission (FTC). Meanwhile, the EU has introduced the Digital Operational Resilience Act (DORA) and the Cyber Resilience Act (CRA) to enforce software security. Australia has announced its national cybersecurity strategy. And Australia, alongside Canada, Germany, The Netherlands, New Zealand, the U.K., and the U.S. has published a guide for software development organizations to ensure their products are both secure by design and by default.
What are the key elements of software supply chain compliance?
- Legal and regulatory requirements. Understanding and complying with local and international laws and regulations is a fundamental aspect. This includes acknowledging intellectual property rights and obligations to credit authors of software code.
- Supply chain transparency. This enables organizations to identify the origin and journey of software products and components. This helps identify any potential security or compliance risks. Documentation and record-keeping play a crucial role in providing evidence of compliance throughout the supply chain.
- Supplier engagement and management. Establishing clear supplier codes of conduct promotes best practices throughout the supply chain. Supplier auditing and risk assessment enable organizations to evaluate the compliance practices of their suppliers. Collaboration with suppliers facilitates knowledge-sharing and encourages compliance.
What are the challenges for software supply chain compliance?
Identifying and mitigating risks. Assessing vulnerabilities in the software supply chain is complex because the volume of components and dependencies is so high, and the rate of change is rapid. Organizations must be aware of them all and must identify potential risks. Implementing due diligence processes helps to minimize these risks.
International regulatory differences. In a global marketplace there are differences in international compliance controls. Organizations must ensure compliance wherever they do business.
Data privacy and cybersecurity. Protecting confidential information, trade secrets, and customer data is paramount for software supply chain compliance, using security measures like encryption, access controls, and vulnerability assessments. Compliance with data protection regulations, such as the General Data Protection Regulation (GDPR), is also crucial.
What are the benefits of software supply chain compliance?
A good compliance strategy will provide clear guidelines and documentation that speed decision-making, and improve software quality and reliability. It will also reduce legal reputational damage resulting from non-compliance while building trust and collaboration with stakeholders.
What are best practices for implementing a software supply chain compliance strategy?
- Invest in a software supply chain management solution. Ensure your chosen solution can generate a software bill of materials (SBOM) that tracks the details and supply chain relationships of software components, their dependencies, and their hierarchical relationships. As governments impose new regulations, SBOMs are vital to application security and compliance.
- Deploy Software Composition Analysis (SCA). SCA tools scan and analyze the open source software in your code base and identify vulnerabilities and malicious packages. The most advanced kinds automatically remediate these threats so all of your code, applications, components, and dependencies are secure.
- Cover all the bases. Look for comprehensive solutions that protect from attacks using malicious open-source packages, Ideally, it should be seamlessly deployed within developers’ workflow and easily integrated into your repositories. Furthermore, you should be able to define policies to allow or block package downloads, based on your organization’s specific needs, and enable continuous monitoring and improvement to apply prompt corrective actions.
- Build a culture of compliance. Leadership should commit to prioritizing compliance throughout their organizations. Employee training and effective communication are vital. Extend this to partners, customers, prospects, and stakeholders, to amplify that you’re taking responsibility for software supply chain security.
Don’t delay.
By embracing software supply chain compliance, organizations can safeguard their operations, mitigate risks, and build strong relationships with stakeholders. Prioritizing software supply chain compliance protects organizations from legal and reputational risks and contributes to improved performance and customer trust.
FAQs
What legal and regulatory requirements should companies consider?
Companies should ensure that they comply with the terms and conditions of all software components and their dependencies in their codebase. They should familiarize themselves with the policies, and cybersecurity strategies wherever they do business, and those of their partners and customers.
How can companies manage cross-border compliance issues?
Developers, DevOps and DevSecOps teams should work with legal teams to ensure that they meet all compliance requirements.
How can organizations implement effective supply chain compliance programs?
Invest in a software supply chain management solution that can provide visibility and control over your supply chain and streamline compliance processes. The solution should be able to handle a wide range of issues and should detect, block and automatically fix vulnerabilities and threats like malicious packages.
What role does technology play in enhancing software supply chain compliance?
Choose a solution that enables you to:
- Generate SBOMs
- Offer scanning and remediation capabilities in the form of SCA
- Define policies based on your organization’s specific needs
- Enable continuous monitoring and improvement to apply prompt corrective actions