NPM Audit: How to Enforce Your Code Security

Table of Contents
Node Package Manager (npm) is a popular utility that allows JavaScript developers to create, use, reuse, manage, and share small pieces of code with others. In v6, npm introduced a new command that lets you assess your package dependencies for security vulnerabilities: npm audit.
In this article, we’re going to demonstrate how to use this new feature to evaluate your dependency tree recursively and safeguard the quality and integrity of your code.
What is NPM audit?
npm audit is a built-in security feature that scans your project for security vulnerabilities, and if available, provides an assessment report that contains details of the identified anomalies, potential fixes, and more.
It checks the current version of the installed packages in your project against known vulnerabilities reported on the public npm registry. If it discovers a security issue, it reports it.
Notably, the report contains the level of severity of the identified vulnerability. The extent of severity is determined by the impact and exploitability of the issue, particularly if it falls on the wrong hands.
The level can be any of the following (alongside their recommended actions):
- Critical—resolve straightaway
- High—resolve as fast as possible
- Moderate—resolve as time allows
- Low—resolve at your discretion
Benefits of npm audit
npm audit offers the following advantages:
- There is a vast community of open source contributors who endeavor to find and address vulnerabilities in npm packages. So, npm audit allows you to leverage their efforts to find and fix security problems in your code, instead of going the tedious route of manually perusing the dependencies in your project to identify security loopholes.
- It identifies the security issues clearly and labels them in terms of the level of severity. This allows you to address them fast and easily.
- If a fix has been published, it provides an out-of-the-box option for resolving the discovered anomalies.
How to run npm audit
Before running a security audit with npm audit, you’ll need to ensure you have npm v6 installed on your system.
You can upgrade by running the following command:
npm install npm@latest –gWhenever you install any package by running npm install, the npm audit command will also run automatically on the background, and output the security audit report.
If you want to run the command manually and check the security status of your installed packages, you can follow this process:
1. Go to the terminal, and on the directory of your installed package, type the following:
cd path/to/name-of-packageThen, press Enter.
2. Confirm that the selected package directory has a package-lock.json file as well as a package.json file, which are required for successfully running npm audit.
Since these files contain the versions of the dependencies used in the project, the npm audit command will use this information to check if there are any reported vulnerabilities with those versions.
3. Type the following command:
npm auditThen, press Enter.
If you want the audit report to be given in JSON format, you can run the following command:
npm audit –jsonAlso, you can specify the audit results to contain a certain level of severity, such as low or higher.
Here is an example:
npm audit –audit-level=critical4. Review the generated vulnerability report and take action, as appropriate.
Security audit report
After running the npm audit command successfully, and if it finds vulnerabilities, it’ll produce an audit report that contains details of the npm security vulnerabilities discovered in your dependency tree.
For example, here is the output we got after running the command on our project:
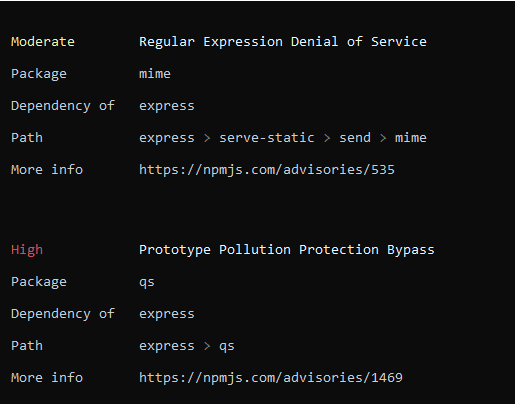
As you can see on the image above, the report includes a description of the severity level of the vulnerability, name of the risky package, any of the package’s dependency, its path, and a link you can use to get more information on the vulnerability.
It may also contain the specific version ranges that include a patch for that vulnerability. Furthermore, it may provide the commands to run to address the security issues.
On the other hand, if no security vulnerabilities are found, npm audit will give that report. This implies that packages with known issues were not discovered in your package dependency tree.
Here is an example:

How to fix the vulnerabilities
To fix the vulnerabilities on the audit report, you can do any of the following:
- Apply the suggested updates automatically
- Perform manual actions to fix them
Let’s talk about each of them.
Apply the suggested updates automatically
If the report reveals the security vulnerabilities in your installed dependencies and new updates are existing, you can simply run npm audit fix to implement the compatible updates automatically.

This subcommand executes a complete npm install command under the hood and sticks to the SemVer-compatible versions. This way, you can run it safely on most of your projects without worrying about introducing any breaking changes.
However, if the update requires moving to a major version, then you’ll need to add the force flag:
npm audit fix –forceHowever, you should be extra cautious with this flag. While patches and minor versions may have backward compatibility, upgrading to major dependency versions may break your code. Therefore, you should refer to the package’s documentation before executing this command.
Apart from the npm audit fix subcommand, you may also execute the commands recommended by npm individually and install the specific updates to the insecure dependencies.
Here is an example:

Since some upgrades may come with SemVer-breaking changes, you’ll get a warning to that effect. In such a case, it may be necessary to make more edits to the code of your package.
Perform manual actions to fix them
If there are no patches for the identified issues, the security audit report will give you more details on how to carry out manual investigations to address them.
Here is an example:
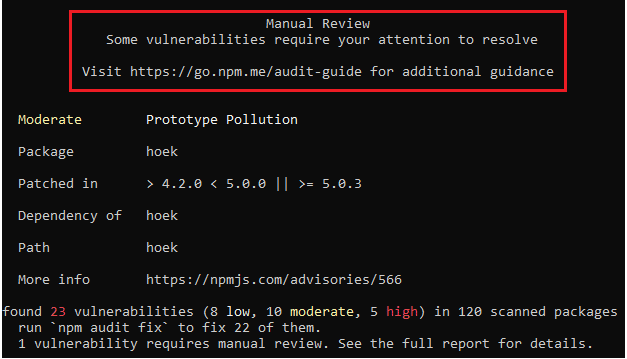
You can take any of the following actions to resolve the vulnerabilities:
i. Look for mitigating factors
In some limited cases, you may continue consuming the package even when the weakness is still existing. For instance, the security risk may only be present on certain operating systems. So, you can check the link on the More info field for any mitigating factors.
ii. Update dependent packages
If a fix has been released, but the packages that depend on the vulnerable package have not been amended to reference the patched version, it may be necessary to undertake some manual interventions.
You can start by locating the package that should be updated by looking at the Path field on the security audit report. This will let you locate the vulnerable package, and the one that depends on it.
Let’s say the path to the identified vulnerability is @name-of-package > name-of-dependent-package > name-of-vulnerable-package, updating name-of-dependent-package to refer to the patched version may solve the security issue.
In such a case, you can go to the repository of the dependent package on the npm public registry and submit a pull request or a merge request.
Once your request to replace the version of the susceptible package with a version having a solution is accepted, you can use npm update to upgrade your installed package.
iii. Fix the vulnerability yourself
If a patch has not been released, you can go to the package repository on the npm public registry and suggest changes that resolve the vulnerability.
You can submit a pull request or a merge request to the package maintainer for the fix to be implemented.
Conclusion
npm audit is a useful feature that can enhance the security of your code. With the command, you can identify vulnerabilities in your applications and get actionable instructions on how to get rid of the risks.
Nonetheless, remember that npm audit may not solve all the security loopholes in your code. You need to implement secure programming practices to ensure your applications are safe from attacks.
Are you letting open-source vulnerabilities go undetected?
Mend Bolt is a powerful free extension that operates in real-time to provide visibility over your open source components within Azure Pipelines or GitHub.
- Get real-time alerts on security vulnerabilities
- Ensure the license compliance of open source components.
- Receive automated open-source inventory reports for every build or project.
Get it now and join thousands of developers who’ve already gained full visibility over their open-source components.






