API Security in a Digitally Transformed World
Table of Contents
One unexpected consequence of the global pandemic is the acceleration of digital transformation across organizations of all sizes. With so many employees working from home, organizations realized they needed to upgrade to a cloud infrastructure to support everyone working remotely. As applications moved from on-premises to the cloud to support these new remote users, organizations needed to think about the APIs and microservices that connected users to essential applications and their impact on Cybersecurity.
What is an API?
An application programming interface, more commonly known as an API, is a software intermediary that allows two applications to talk to each other. Think of an API as a user interface but instead of a human user, the user is a machine. APIs allow different devices to connect with each other across disparate compute environments.
Another way to think of this is to imagine an API as a waiter at a restaurant. You, the diner, choose dishes off a menu. When you place your order, the waiter delivers that order to the kitchen. The kitchen prepares the meal and returns it to the waiter to serve to you. You don’t need to know how the chef prepares the saffron-flecked mussels in salt-cod foam, you only know that it’s delicious.
API examples
APIs are everywhere. When you check the weather on your phone, your phone accesses weather information through an API to provide you with a snippet of weather data. When you stream Spotify or Netflix, content is distributed to your device via an API. When you book a hotel room or an airline ticket, your app uses the APIs of a number of hotels or airlines to aggregate data about availability and rates. Accessing your bank account balance through an app on your phone? You got it: an API is doing the work. In these ways and more, APIs link applications, data, and devices to deliver data and create an interconnected world.
Why is API security important?
APIs are the connective tissue linking ecosystems of technologies and organizations. They also allow businesses to monetize data, form profitable partnerships, and open pathways of innovation.
Unfortunately, when it comes to application security best practices, APIs are sometimes overlooked. Though APIs are key to digital transformation, they are simultaneously one of the biggest cybersecurity attack vectors and the most often neglected. The average enterprise has approximately 1,000 applications, and the expansion of endpoints creates new attack surfaces. Despite this, many organizations still struggle to secure APIs.
Why are so many organizations still struggling? There are two main reasons organizations are struggling to secure their APIs: inertia and difficulty.
All too often, API security is simply overlooked. It is too often seen as separate from the overall application security posture of an organization. In some cases, simple token-based authentication is set once and then forgotten.
Additionally, APIs are hard to defend because they are highly exposed to the outside world. The amount of data that passes through the application layer makes it attractive to malicious actors. Furthermore, API hacking does not require advanced technical capabilities. Even relatively inexperienced attackers can use basic tools to discover and exploit API traffic to perform credential stuffing attacks, exfiltrate databases, change account values, or conduct denial of service attacks on critical applications.
API security maturity model
Understanding identity is key to API security. Hackers frequently impersonate users. The API Security Model, based on the Richardson Maturity Model, describes API security in increasing levels of security, complexity, and efficiency. The more evolved API security is, the more it focuses on identity.
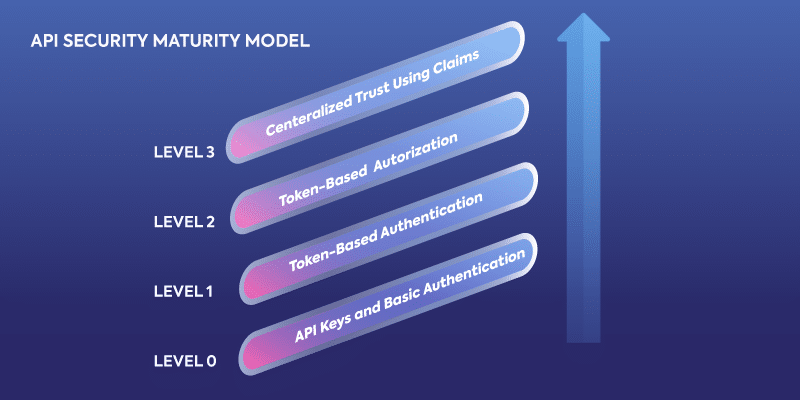
The four levels of API security are as follows:
- Level 0 – API keys and basic authentication. Level 0, which is the level of security that most APIs adopt, uses basic authentication or API keys inserted in the header or body of the URL of the API request to verify API calls.
- Level 1 – Token-based authentication. This level, which builds on Level 0, uses tokens to establish authentication.
- Level 2 – Token-based authorization. Again, this builds on levels 0 and 1, but adds OAuth, an authorization standard that requires client requests be authorized by an OAuth server, to establish identity.
- Level 3 – Centralized trust using claims. Level 3, the most mature API security level, builds on the previous three levels but adds both OAuth and OpenID Connect to verify identity.
Identity is crucial. The most highly evolved API security focuses on identity, that is, ensuring that the person who is making the request is actually who they claim to be. In a digital world where trust is subjective, organizations must do everything they can to maintain and verify it.
API security best practices
Whether on your corporate network or in the cloud, securing your APIs is critical to your organization’s overall security posture in a digitally transformed world. Constant vigilance should be your mantra. We also recommend beginning with several best practices for securing your APIs:
- Adopt a holistic approach to API security
- Focus on identity
- Monitor and set rate limits
To learn more about these best practices for API security and how to make smarter security decisions, download our white paper, Five Principles of Modern Application Security Programs.


