Dynamic Application Security Testing: DAST Basics
Table of Contents
Application security testing (AST), which are tools that automate the testing, analyzing, and reporting of security vulnerabilities, is an indispensable part of software development. In a modern DevOps framework where security is shifted left, AST should be thought of as compulsory. And this has never been more important when you consider that Forrester reports the most common external attack method continues to be application weaknesses and software vulnerabilities.
The AST market is broken down into four broad categories:
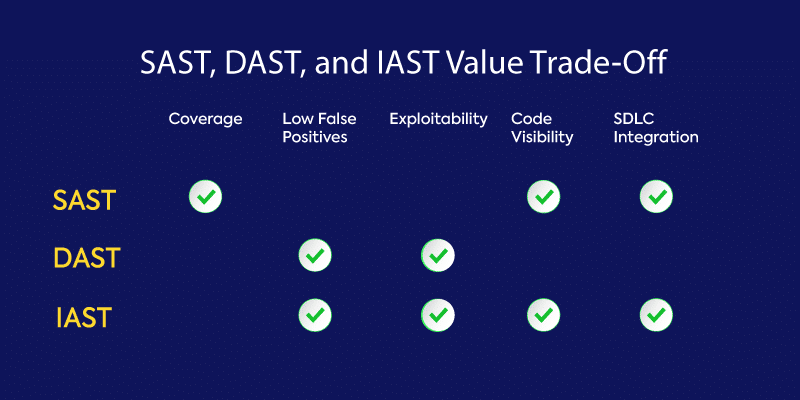
- Static application security testing (SAST) is white-box testing that analyzes source code from the inside while components are at rest.
- Dynamic application security testing (DAST) is a type of black-box security testing in which tests are performed by attacking an application from the outside.
- Interactive application security testing (IAST) works from within an application through instrumentation of the code to detect and report issues while the application is running.
- Software composition analysis (SCA) scans your code base to provide visibility into open source software components, including license compliance and security vulnerabilities.
Each type of AST tool focuses on a slightly different aspect of application security. In this blog, we look at dynamic application security testing (DAST). We define what DAST is, how it works, and its pros and cons.
What is DAST?
DAST, sometimes called a web application vulnerability scanner, is a type of black-box security test. It looks for security vulnerabilities by simulating external attacks on an application while the application is running. It attempts to penetrate an application from the outside by checking its exposed interfaces for vulnerabilities and flaws.
The dynamic part of DAST’s name comes from the test being performed in a dynamic environment. Unlike SAST, which scans an application’s code line by line when the application is at rest, DAST testing is executed while the application is running. This is not to say that testing is performed while the application is in production. While DAST can be used in production, testing usually is carried out in a QA environment.
DAST is extremely good at finding externally visible issues and vulnerabilities. This includes a number of security risks from OWASP’s top ten, such as cross-site scripting, injection errors like SQL injection or command injection, path traversal, and insecure server configuration.
One of DAST’s advantages is its ability to identify runtime problems, which is something SAST can’t do in its static state. DAST is excellent at finding server configuration and authentication problems, as well as flaws that are only visible when a known user logs in.
How does DAST work?
DAST works by implementing automated scans that simulate malicious external attacks on an application to identify outcomes that are not part of an expected result set. One example of this is injecting malicious data to uncover common injection flaws. DAST tests all HTTP and HTML access points and also emulates random actions and user behaviors to find vulnerabilities.
Because DAST has no access to an application’s source code, it detects security vulnerabilities by attacking the application externally. DAST does not look at code, so it can not point testers to specific lines of code when vulnerabilities are found.
Security experts are heavily relied upon when implementing DAST solutions. For DAST to be useful, security experts often need to write tests or fine-tune the tool. This requires a solid understanding of how the application they are testing works as well as how it is used. Security experts also must have a strong knowledge of web servers, application servers, databases, access control lists, application traffic flow, and more to effectively administer DAST.
Though they may sound similar, DAST differs from penetration testing (or pen testing) in several important ways. DAST offers systematic testing focused on the application in a running state. Pen testing, on the other hand, uses common hacking techniques with the owner’s permission and attempts to exploit vulnerabilities beyond just the application, including firewalls, ports, routers, and servers.
DAST pros and cons
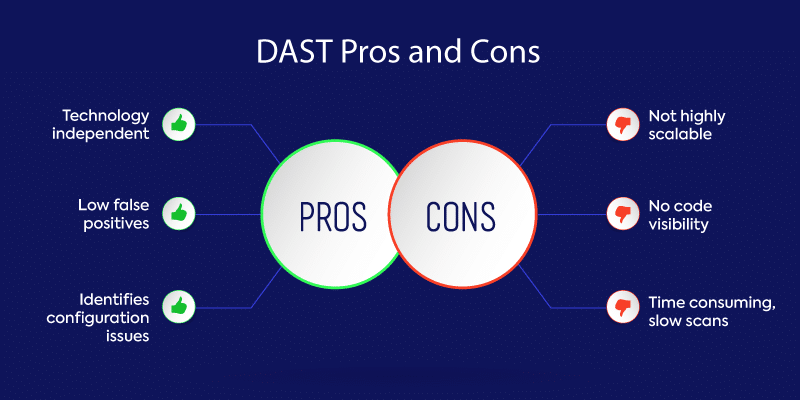
DAST is a valuable testing tool that can uncover security vulnerabilities other tools can’t. Though DAST excels in certain areas, it does have its limitations. Let’s look at the top pros and cons for this technology.
Pros
#1 Technology independent
Because DAST doesn’t look at source code, it is not language or platform specific. Not being limited to specific languages or technologies allows you to run one DAST tool on all your applications.
#2 Low false positives
Based on OWASP’s Benchmark Project, DAST has a lower false positive rate than other application security testing tools. Testers can zero in on real vulnerabilities while tuning out the noise.
#3 Identifies configuration issues
DAST excels at finding security vulnerabilities that occur only when the application is operational. In addition, DAST attacks an application from the outside in, placing it in the perfect position to find configuration mistakes missed by other AST tools.
Cons
#1 Not highly scalable
One of the main downsides to DAST is its heavy reliance on security experts to write effective tests, which makes it very difficult to scale.
#2 No code visibility
DAST does not have any visibility into an application’s code base. This means DAST can’t point developers to problematic code for remediation or provide comprehensive security coverage on its own.
#3 Slow scans
DAST is not known for its speed, and many users report scans taking too long. Forrester estimates that DAST scans can last as long as 5-7 days. In addition, DAST scans typically find vulnerabilities later in the software development life cycle (SDLC), when they are more costly and time consuming to fix.
DAST: One piece of your application security puzzle
In a modern DevOps practice, security and developer teams need testing solutions that help secure applications without slowing down development. In this sense, DAST is a powerful tool. In fact, after SAST, DAST is the second largest segment of the AST market. Forrester research reports that 35% of organizations surveyed already use DAST and many more plan to adopt it.
When it comes to application security, however, there is no one tool that can do it all. Though DAST fills an important function in finding potential run-time errors in a dynamic environment, it will never find an error in a line of code. DAST doesn’t provide comprehensive coverage on its own.
For this reason, most organizations need a number of AST tools working in concert to effectively reduce their security risk. DAST excels in looking at external attack methods. SAST finds coding errors by scanning the entire code base. Together with an SCA solution to handle your open source software, they provide the comprehensive testing strategy your organization needs.


