All About IAST — Interactive Application Security Testing

Table of Contents
Because applications and software vulnerabilities are the most common external point of attack, application security is a top priority for most organizations. An essential component for reducing this risk is application security testing (AST).
In this blog, we focus on interactive application security testing (IAST), the relative newcomer in the AST market. IAST follows on the heels of the better-known and more mature static application security testing (SAST) and dynamic application security testing (DAST) tools, combining some elements of both.
It’s important to understand where IAST fits in the spectrum of AST tools so that you can ensure your applications are thoroughly tested and as secure as possible before releasing them into the world. Like all AST tools, IAST has its benefits and limitations, and this blog will explore both.
What is IAST?
IAST is an AST tool designed for modern web and mobile applications that works from within an application to detect and report issues while the application is running. To fully understand IAST, you first need some background on SAST and DAST.
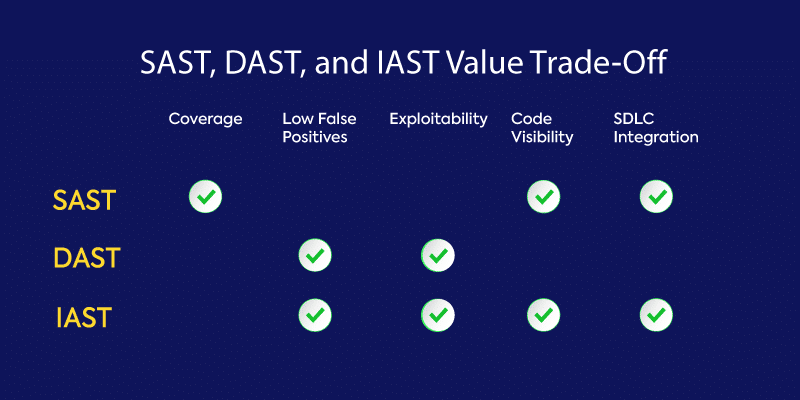
SAST, a type of white-box testing, analyzes source code at rest from the inside out. Though the most mature and easiest to deploy of the AST tools, scans are slow and prone to high false-positive rates when identifying potential vulnerabilities.
DAST, a type of black-box testing, looks for vulnerabilities by simulating external attacks on an application while it is running in a test environment. It attempts to penetrate an application from the outside by checking its exposed interfaces for vulnerabilities and, as a result, provides no visibility into an application’s code. DAST is hard to automate and scale because experienced security professionals are required to write these test tools for them to be useful.
IAST was developed as an attempt to overcome some of the limitations of SAST and DAST. Like DAST, testing occurs in real time while the application is running in a QA or test environment. Unlike DAST, however, IAST can identify the problematic line of code and notify the developer for immediate remediation.
As with SAST, IAST also looks at the code itself, but it does so post-build, in a dynamic environment through instrumentation of the code. IAST can be easily integrated into the CI/CD pipeline, is highly scalable, and can be automated or performed by a human tester.
How does IAST work?
IAST typically is implemented by deploying agents and sensors in the application post build. The agent observes the application’s operation and analyzes traffic flow to identify security vulnerabilities. It does this by mapping external signatures or patterns to source code, which allows it to identify more complex vulnerabilities.
IAST test results are usually reported in real time via a web browser, dashboard, or customized report without adding extra time to the CI/CD pipeline. IAST results can also be combined with other issues tracking tools.
The biggest differentiator for IAST is that, unlike SAST and DAST, it works from inside the application. However, IAST doesn’t scan the entire codebase. Instead it tests functionality only at certain points as defined by the tester, which makes it significantly faster to execute than SAST but doesn’t provide the complete coverage SAST does.
IAST pros and cons
IAST is a developer-centric technology that helps organizations shift left when addressing security testing. Even though IAST has many benefits, it’s not without its flaws. Let’s look at the pros and cons of IAST.
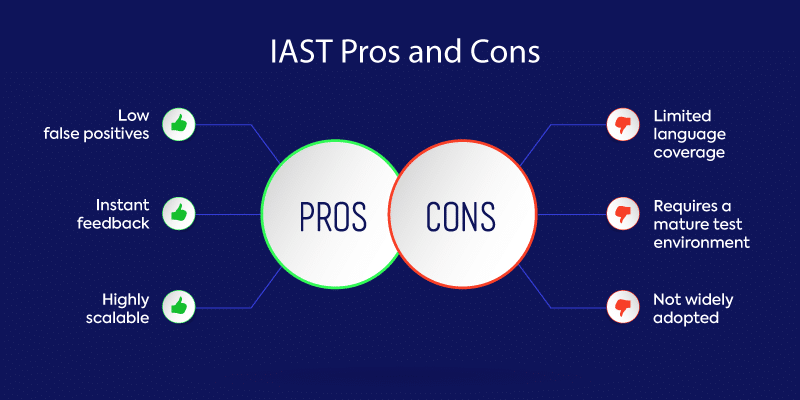
Pros:
1: Low number of false positives
IAST has an extremely low false-positive rate, unlike SAST, which has a notoriously high false-positive rate. A significant number of organizations face thousands of daily security alerts. With this volume, accuracy in testing is critical in cutting down the noise and reducing alert fatigue.
2: Instant feedback
To keep up with the pace of development these days, developers demand fast testing solutions with no lag time. IAST delivers speed by providing test results directly to developers in real time. IAST also integrates well with CI/CD tools. Remediating vulnerabilities and checking in clean code early in the software development life cycle (SDLC) helps organizations save time and money.
3: Highly scalable
IAST is highly scalable and is easily deployed to every developer across an organization. Test results direct developers to specific lines of problematic code for immediate remediation without requiring the intervention of a security professional.
Cons:
1: Limited language coverage
Because IAST is embedded in the application it is testing, it is language-specific and has a server-side architecture. IAST lacks coverage across certain languages and only supports modern technology frameworks. On its own, IAST doesn’t provide enough coverage, and it works best when combined with other AST solutions.
2: Requires a mature test environment
To gain the most value from IAST, organizations need a mature and well-defined test environment. IAST requires a modern software development environment and architecture.
3: Not widely adopted
Even though IAST has been around for several years, it still hasn’t found a stronghold in the market. Whether this is because it doesn’t provide enough coverage on its own, there’s no measurable return on investment, or it hasn’t found the right use cases has yet to be determined.
IAST: Finding a balance
IAST can be an effective AST tool, and its dynamic nature offers many benefits when developing secure applications. Compared with SAST and DAST tools, IAST provides the fastest and most accurate results. It is also easily integrated into CI/CD build pipelines.
Unfortunately, IAST has its limitations. It may not cover all the languages and technology stacks you use in your organization. Unlike SAST, it does not look at every line of code. The bottom line is IAST works best when used alongside other SAST and DAST solutions.
Choosing the right AST solution involves finding a balance between speed, accuracy, coverage, and cost. IAST is a powerful tool to have in your arsenal, but unfortunately, it can’t do it all on its own.


