The Internet of Things Is Everywhere. Are You Secure?
Table of Contents
From smart homes that enable you to control your thermostat from a distance to sensors on oil rigs that help predict maintenance to autonomous vehicles to GPS sensors implanted in the horns of endangered black rhinos, the internet of things is all around you. The internet of things (IoT) describes the network of interconnected devices embedded with sensors, software, or other technology that exchange data with other devices and systems over the Internet.
According to Gartner research, 35 billion devices will be connected to the internet in 2021, and that number will more than double in the next few years to reach 75 billion connected devices by 2025. This means that currently there are three IoT devices for every one human on the planet. Whether these devices are smart (they have the ability to compute) or dumb (they report data to a centralized location with little or no processing power), this market is experiencing phenomenal growth.
With the increase in connected devices comes an increase in IoT attacks. In 2019 alone, attacks on IoT devices increased by 300%. This growth has also given rise to cybersecurity challenges. With the increase
The technical challenge of IoT security
In the DZone Edge Computing and IoT report published in 2020, developers were asked to rank the top 15 most pressing technical challenges of IoT. Security came in as the number one most challenging issue facing this market today, beating out unpredictable physical environment, network bandwidth availability, latency, and device unreliability by a wide margin.
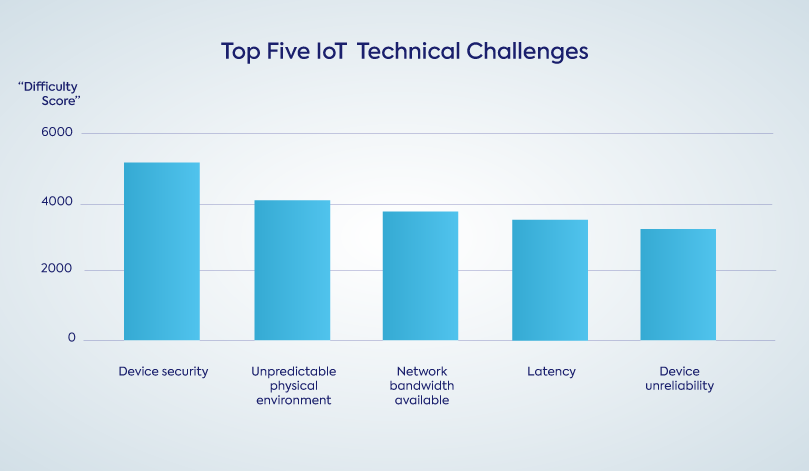
Source: DZone’s Edge Computing and IoT, 2020
When you consider that IoT devices are controlling autonomous vehicles, drug pumps, manufacturing operations, and even the camera on your virtual assistant, you begin to realize security is important. It’s more than someone hacking into your smart light bulbs and turning on all the lights in your home. Security for IoT means your municipal water source or an implantable cardiac device or, in the case of the Mirai botnet attack, vast swathes of the internet.
Why do developers say security is their biggest IoT challenge? The threat landscape for IoT is extremely broad and complex, and it involves both physical device security and network security. Furthermore, to fully secure IoT devices, you need to address both hardware and software.
Network security is a challenge because the proliferation of devices each with their own IP address means you can’t slap up a perimeter firewall to block all suspicious or unknown web traffic. Some best practices to secure IoT at the network level include map and monitor all connected devices, use network segmentation to prevent the spread of attacks, ensure your network architecture is secure, and disable any features or services that you aren’t using.
Device security brings its own difficulties. First, with billions of connected devices, there is a vast range of hardware. As a result, no one-size-fits-all approach will work. Despite the heterogeneity, some best practices include discovering the devices on your network for complete visibility and then actively monitoring these devices. After all, you can not secure a device if you don’t know it exists. Staying current with firmware patches and updates is also key to enabling robust security.
Don’t forget the application layer
Because we refer to IoT as ‘connected devices,’ we tend to think of this technology in terms of hardware – watches, appliances, sensors, monitors – but don’t forget that each of these devices contains an application layer that also needs to be secured.
The application layer is the most attacked in the enterprise stack. For IoT, application security is even more important because application layer protocols form the foundation of communication between different IoT devices and an organization’s cloud or edge infrastructures.
Both secure coding and application security testing best practices need to be applied to the development of the application on every IoT device. In addition, IoT applications should be exposed to the same rigorous testing as any other application. Security scanning tools such as static application security testing (SAST) and software composition analysis (SCA) should be the standard.
Open source and IoT devices
Greater than 90% of developers rely heavily on open source components when creating IoT applications. This should come as no surprise as a wide range of open source tools, components, platforms, and frameworks are available for every niche area of IoT technology. Linux is the top operating system for IoT devices, and 93% of databases used in IoT applications are open source.
Because of the widespread use of open source in IoT, special attention must be paid to open source security, both when developing an IoT application and when IoT devices are in production. Open source vulnerabilities are published and publicly available for anyone to see – including hackers. If you’re not scanning the open source in your applications and monitoring it in production, then you’re not securing your IoT devices.
C and IoT devices
For IoT devices, C and C++ are the predominant programming languages. C is particularly attractive for IoT devices such as sensors that detect temperature or humidity, because simple microcontrollers don’t have operating systems and C can work directly with RAM. For devices performing slightly more complex tasks that still require a small footprint, like turning on smart lights in your home, C++ is an attractive alternative.
When looking for a software composition analysis solution to scan your IoT application, remember that not all SCA solutions can scan programming languages that lack package managers like C and C++ do. When searching for a solution to scan the open source code for your IoT application, make sure you choose one that is able to scan source code and supports all required languages.
Best practices for IoT security
Now that we’ve highlighted some of the main concerns for IoT security, here are some best practices you can put in place now to ensure your devices are as secure as possible:
- Basic security hygiene: It’s been said a thousand times, but it still holds up: change those passwords! Practicing basic security hygiene should be rote by now. Default passwords are bad, and you should be using strong, unique passwords. Disable those features you’re not using. Implement identity management best practices through authentication and authorization methods. It’s basic but it works.
- Discovery: It is important to understand what devices are on your network. If you don’t have a comprehensive inventory of the components in your IoT environments you won’t be able to apply patches and remediate vulnerabilities.
- End-to-end protection: Secure your physical infrastructure – both your network and devices – but also don’t forget about software vulnerabilities. Remember that open source code plays a big role here, so stay on top of those vulnerabilities by scanning and monitoring these components often, particularly as new vulnerabilities are disclosed.
- Policy and segmentation: Don’t allow malicious actors to exploit holes in your organizational security by jumping from device to device. You should automate security policies that define acceptable communication, blocking anything that is out of policy. For example, a point-of-sale terminal might be allowed to send inventory data to a particular database, but not communicate with other devices.
- Monitoring and threat prevention: Monitor your IoT devices to learn how they connect and act within your network so you can identify unusual behavior and detect any anomalies.
A holistic approach to IoT security will help you navigate the potential pitfalls around complex hardware and software security issues.
A safer internet of things
Everyone agrees that when it comes to any technology, more security is better than less security. IoT is no different. To that end, both California and Oregon have recently enacted legislation governing the security of connected devices and the Internet of Things and users’ privacy. It is believed that the US federal government isn’t far behind.
IoT technologies are becoming more prevalent in all industries and more integrated into our personal lives. They offer tremendous advancements that improve our health and wellbeing and offer significant convenience in our daily living. These advantages must be weighed against the security and privacy issues endemic to connected IoT devices. The IoT threat landscape is extremely wide, complex, and not always properly managed. The machines are here to stay. Wouldn’t we all be happier if they were also more secure?


