Shift-Left Testing and Its Benefits

Table of Contents
Testing practices have been shifting left in the software development process due to the growing challenge of developing and delivering high-quality, secure software at today’s competitive pace. Agile methodologies and the DevOps approach were created to address these needs.
In this post, we’ll map out the basics of shift-left practices in the DevOps pipeline and discuss how to shift left your open source security and compliance testing.
What does shift left mean?
Traditionally, typical development and quality assurance cycles were organized around ‘base levels’. Developers would work on a base level and when it was done, it was passed on to the QA team, who would test that base level and give the results back to the development team to fix. Then the cycle would be repeated as necessary.
Nowadays, the software development industry has learned that fixing bugs detected earlier in the process is easier and cheaper. New strategies of shifting tests earlier in the software development lifecycle (SDLC) have been introduced to help identify issues as early as possible. Early detection accelerates the process of taking corrective steps, thereby reducing the time and cost of fixing these issues. Shifting left means testing as early as possible — or moving the process to the left in the DevOps pipeline.
Shift left vs shift right
Imagine a development life cycle as a line or continuum, with the start of the process on the left, the completion of the process — the release of the software or application — on the right, and all the various stages in between, as in the diagram below.
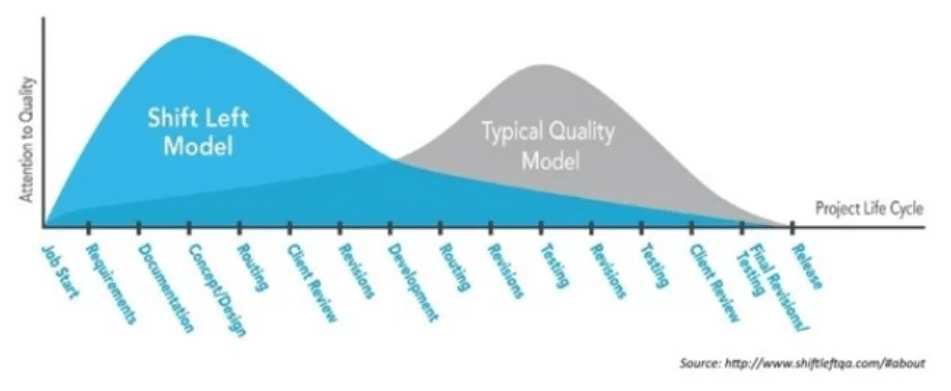
Traditionally, security testing waited until the bulk of the development was done, towards the right of the process, as indicated above. The problem with that is that if any issues are identified, the process has to revert to the beginning to revise the code base, the components, and the dependencies that are causing concern before testing again. And if problems remain, this entire procedure has to start again.
That’s pretty cumbersome. In response, development teams have begun to shift security testing as far left along this line as possible, to detect and remediate flaws, vulnerabilities, and threats as soon and as quickly as possible. This shift enables development teams to test code earlier, receive and act on feedback quicker, review results, and make changes more easily. Ultimately, shifting left can reduce development costs, speed time to market, and cut down on errors.
Conversely, shift-right testing refers to post-production testing on the right of the development process. Shift-right testing enables teams to test a fully functioning application and observe user behavior. This helps improve software quality, particularly in terms of performance and usability.
Shift left and DevOps
Shifting left is a critical part of the DevOps approach, which calls for testing software early and often. Shift left integrates testing into your DevOps pipeline so that defects are detected early, when they are easier and less expensive to fix. Testing, feedback, and revisions are performed continuously, on a daily basis. Like other DevOps processes, this promotes agility and lets the project team scale their efforts to boost productivity.
Delayed detection of issues can be very costly. According to IBM’s most recent Cost of a Data Breach Report 2022, featuring research by the Ponemon Institute, the cost of the average data breach costs rose from $4.24 million in 2021 to $4.35 million in 2022, the highest average total cost in the 18-year history of this report and a rise of 12.7 percent from $3.86 million in 2020. This doesn’t even include the pressure of meeting — or missing — release dates. As the software development stages progress, the cost of addressing any uncovered bugs also rises, often exponentially.
Shift left is all about uncovering as many issues as possible as early as you can in the software development process, so the cost of fixing them is under control. By testing often, your team and stakeholders can ensure better visibility and control over the current state of the code and make informed decisions throughout the project. But is shift left testing, in its traditional manner, enough today?
Shifting open source testing left
Originally, shift-left testing was focused on testing proprietary code. But what about open source and third-party components? When do you check that your software projects don’t contain problematic licenses or outdated or vulnerable versions of open source components?
Open source components have become the basic building blocks of today’s software products, used at scale by almost all commercial software companies. As a result, it’s crucial to include open source security and compliance testing in shift-left practices.
This requires applying a DevOps strategy to open source security and compliance management by integrating Software Composition Analysis (SCA) tools into the coding and build processes, to test open source components early and often.
Shifting security testing left
When it comes to security testing, open source security is unlike proprietary code. Issues are detected by a large, active, capable, and committed community that continuously detects and publishes new open source vulnerabilities.
In 2021 alone, nearly 10,000 known security vulnerabilities were detected in open source components. The continuous rise in open source vulnerabilities has driven increased use of automated detection and remediation tools that align with a shift-left strategy — and which test open source components as early as possible in the development process.
Tools that shift security left
There are a variety of tools that help shift security left. Each has its own benefits and they can be deployed to complement each other to reinforce the security of your code base, software, and application components and dependencies. The main tools of this kind are:
Static Application System Testing (SAST) tests the proprietary source code of the application to detect vulnerabilities. It analyzes the code when it is static — at rest rather than live. However, you can also run SAST scans on code in progress. A new generation of SAST tools, like Mend SAST, also enables users to automatically remediate flaws and vulnerabilities.
Dynamic Application Security Testing (DAST) tests code for runtime vulnerabilities and security issues like SQL injections. DAST is conducted after SAST along the SDLC line. It checks for vulnerabilities by simulating external attacks on an application in a test environment but provides no visibility into an application’s code.
Interactive Application Security Testing (IAST) seeks to combine the benefits of SAST and DAST. Like DAST, testing happens while the application is running in a QA or test environment but IAST can identify the problematic line of code and notify the developer for immediate remediation.
Software Composition Analysis (SCA) scans open source code, components, and dependencies for flaws and vulnerabilities that pose a risk and automatically remediates them as seamlessly as possible, without interrupting developers’ workflow.
Secrets detection. These tools examine all the changes made within a project to make sure that no secrets or vulnerabilities remain that were not detected by SAST scans. They can also identify issues that could compromise security, such as database credentials and API keys.
Dependency scanning focuses entirely on automatically finding vulnerabilities in dependencies. Usually deployed during the development and testing phases, dependency scanning enables you to check open source libraries for known vulnerabilities.
Runtime Application Self Protection (RASP) detects attacks in real time from the inside and prevents these attacks by automatically re-configuring code in response to certain conditions. RASP scans only occur when the application starts running. They analyze the behavior of the application within its context and they protect applications against an increasing range of threats, like SQL/command injections, cross-site scripting (XSS), data exfiltration, account takeovers, and security bots and scanners, among others.
Shifting compliance left
Open source license compliance is also critical when implementing a shift-left strategy in open source management. Organizations must ensure that all open source components are licensed properly. No license means it is merely a public code, but the author still holds the copyright for it and you cannot use it. In addition, compliance requires that the open source licenses in your codebase are compatible and that you can comply with them.
Automate to shift left
As well as enabling teams to test earlier, shifting left enables them to test often, and even continuously in some cases. This iterative approach lends itself to automation, and there are now tools available that provide automated testing as they shift it left toward the start of the SDLC.
Automation is becoming increasingly important to ensure that teams are not overwhelmed with manual testing and remediation of components and dependencies within every new feature and application that developers launch.
It takes this burden away from developers while maintaining and often improving the detection, prioritization, and remediation capabilities needed to secure software and applications.
There are some significant benefits that arise from automating the shift left. Firstly, human error is eliminated. Secondly, automation enables multiple tests to be performed simultaneously and therefore means that a much higher volume of components and dependencies can be tested. Thirdly, by removing this time-consuming manual task, automation boosts productivity by freeing developers to focus on what they do best — develop new apps and improve current ones. This productivity is further increased because fewer production issues will arise, as fewer flaws will remain in your code base. Ultimately, it means you can accelerate your delivery of software and applications, but do so more securely and with more confidence, without increasing any risks of defects, vulnerabilities, or any other issues.
Benefits of a shift left approach
Better security. More confidence
Shifting security left offers the potential and opportunity to increase and repeat testing throughout the SDLC. This makes security more thorough and more robust and gives you much more confidence in your code base, your software, and your applications. When you shift left, you can be increasingly certain that you’re shipping secure, high-quality software and applications.
Ease and efficiency
When bugs are detected earlier in the SDLC, they are easier to fix. When testing is shifted left, issues can be found and addressed before they escalate, so they’re caught before they cause problems. It also means they’re addressed before production is complete, which is when it takes longer to mend flaws and vulnerabilities and requires more time and resources to do so. Consequently, you can be more confident that your product can be delivered in as timely and as efficient a manner as possible.
Improved quality
The earlier you find and fix issues, the smaller the risk they pose and the chance of damage is minimized. Consequently, the quality of your output is improved. More stringent and earlier testing, therefore, results in a better, more reliable, and more stable end product for users.
Lower costs
As shifting left makes it easier and more efficient to detect threats and address them, it ultimately means fewer resources and less time are needed to remediate them. This reduces the overall cost of development.
Speed
Shifting left enables issues to be found and addressed quickly and much earlier in the SDLC. Flaws and vulnerabilities are fixed before they can be exploited and before damage can be done to your code, software, and applications. It also means that you can improve productivity by accelerating production and speeding up the time to market of your software and your applications.
Implementing a comprehensive shift-left strategy
Shift-left testing is an important part of a mature DevSecOps program and has gone far beyond early QA testing. In order to ensure the security of your software products while keeping up with tight delivery deadlines, the shift-left approach must also be implemented in application security practices.
As our software development systems become more complex and layered, spanning across microservices, the cloud, and containers — to name just a few platforms — a solid shift-left strategy must address all platforms and languages.
This requires adopting automated testing tools that can be easily integrated early in the development process — but that’s not enough. It’s crucial to ensure that these tools are implemented by all teams. That means the tools need to fit seamlessly into development and DevOps environments so that they don’t interrupt or delay development.
Another important aspect of an effective shift left-testing strategy is ensuring early vulnerability prioritization and remediation. As organizations invest in a variety of automated testing tools, it’s important to choose those that go beyond vulnerability detection and deliver prioritization and remediation. Otherwise, your shift left strategy is incomplete, leaving you with an ever-expanding laundry list of vulnerability alerts.
Embracing the shift-left testing approach
As the threat landscape evolves, development environments expand, and release schedules become tighter and tighter, we must continuously update our shift-left strategies.
Shift-left tools and processes that might have worked a few years ago are no longer enough to ensure quality, security, and speed. Organizations need to make sure that their shift-left strategies remain up-to-date and can keep up with today’s application security challenges.
Shift Left Testing FAQs
Why should organizations shift left?
Shifting left makes the detection and remediation of software vulnerabilities faster, easier, and cheaper, and allows you to have more confidence in your code, software, and applications. It also enables faster and more agile development, increases collaboration, and results in the production of higher-quality products.
What is necessary to shift left successfully?
You need a combination of practical and cultural changes to shift left successfully. These include:
- Identifying and implementing the use of AST tools that best meet your needs
- Ensuring that these tools can be integrated into existing workflows to make them seamless to use
- Automating the shift- left processes wherever possible
- Educating teams on the importance of shifting left, why and how to do so, and encouraging adoption of your chosen tools




