Vulnerability Management — What You Need To Know

Table of Contents
Vulnerability management is becoming increasingly important to companies due to the rising threat of cyber security attacks and regulations like PCI DSS, HIPAA, NIST 800-731 and more. Vulnerability management is a comprehensive process implemented to continuously identify, evaluate, classify, remediate, and report on security vulnerabilities.
While vulnerability management isn’t a novel concept for most companies, it’s become clear that formerly accepted practices — such as quarterly vulnerability scans and remediation management plans — are severely deficient means of defense.
Today, minimizing your attack surface and overall risk exposure requires a continuous approach that increases visibility over vulnerabilities and enables rapid remediation.
What is Vulnerability Management?
While the term vulnerability management is often used interchangeably with patch management, they are not the same thing. Rather, the decision to use a patch, or not, falls within the broader context of vulnerability management.
Vulnerability management includes much more than scanning and patching vulnerabilities. It requires a holistic view in order to make informed decisions about which vulnerabilities to address first and how to mitigate them.
Security scans can no longer be a periodic occurrence – they must be run continuously, enabled by automated tools. In order to address the increased security debt that most organizations are experiencing due to the rising number of vulnerabilities, a prioritization and remediation strategy must be implemented. In addition, security, development, and DevOps teams must all take part in the vulnerability management efforts in order to ensure threats are mitigated swiftly and efficiently. All of these moving parts must be detailed clearly as part of a comprehensive vulnerability management policy.
The Four Stages of Vulnerability Management
#1 Identification
The first stage in your vulnerability management program will be to identify all of the vulnerabilities that exist across your IT ecosystems. In order to achieve this you will need to define your IT assets and find the right vulnerability scanners for each asset.
The vulnerability scanner you’ll use to identify vulnerabilities in your network and in your applications will not be the same. When it comes to application security, you will need to use multiple AST (application security testing) tools in order to detect vulnerabilities in your proprietary code and open source libraries.
This is an essential part of vulnerability management and one that is becoming increasingly challenging as organizations’ IT ecosystems become more expansive, complex, and interconnected.
According to the Center for Internet Security, organizations should perform automated vulnerability scans at least once a week. More frequent scanning will give you greater clarity on the progress of your remediation and help you identify new risks based on updated vulnerability information.
#2 Evaluation
After you’ve identified the vulnerabilities that exist across your systems, the next step is to evaluate the risks they pose and determine how to manage them. While it’s important to understand the risk ratings that your vulnerability management solution provides, such as Common Vulnerability Scoring System scores, you will also want to understand other real-world risk factors.
Some additional factors to consider include:
- How easily could someone exploit this vulnerability, and is there published exploit code available?
- Does the vulnerability directly impact the security of our product?
- What would the business impact be if this vulnerability was exploited?
- Do we have any existing security protocols that would reduce the likelihood/consequence of these vulnerabilities being exploited?
It’s also important to know whether any identified vulnerabilities are false positives. With tools and techniques that enable vulnerability validation, such as penetration testing, you can identify false positives and focus on the vulnerabilities that pose the biggest risk to your organization.
#3 Remediation
After you’ve identified and evaluated vulnerabilities, the next step is to determine how to prioritize and address them.
Your vulnerability management solution will likely recommend which remediation technique you should use for each vulnerability. It’s best that your security team, system owners, and system administrators weigh-in to determine the right strategy.
There are three general routes you can take:
- Remediation: Completely preventing exploitation by patching, correcting, or replacing code that contains a vulnerability.
- Mitigation: Reducing the probability or impact of a vulnerability. This is usually a temporary solution that organizations use until they can remediate the vulnerability.
- No action: Acknowledging and accepting the vulnerability. Organizations typically only do this when the cost of remediating the vulnerability is much higher than the consequences of it being exploited.
After you’ve finished the remediation process, you can check to see that the vulnerability was completely resolved by performing another scan.
#4 Reporting
By making vulnerability assessments a routine practice, you’ll gain greater insight into the efficacy, speed, and cost of your vulnerability management program.
Most vulnerability management systems let you export the data from your various vulnerability scanners so your security team can more easily understand the security posture of each asset and track it with time to identify trends like increased vulnerability detection or decreased remediation velocity.
Consistent reporting will help your security team to comply with your organization’s risk management KPIs as well as regulatory requirements.
Vulnerability Management Metrics
Measurement and metrics are another important part of a vulnerability management policy — organizations must make sure that the detection and remediation tools that they are using are producing comprehensive and up-to-date reports.
Key vulnerability management metrics organizations should make sure that they’re tracking include time to detection, time to remediation, patching rate, and more. This helps teams make sure that they are keeping up with their KPIs and provides managers and stakeholders with the information that they need to keep up with their security profile and continue to perfect their security strategies.
Setting Up a Vulnerability Management Policy
Compliance with cross-industry standards like ISO 27002 have required organizations to implement a vulnerability management policy for years. Today’s evolving threat landscape requires companies to ensure that their vulnerability management policy keeps up with security, as their software development and delivery ecosystems become more complex.
Vulnerability management policies must cover all four stages listed above, and include continuous security scanning across all parts of the software development life cycle, with both AST (application security testing) tools and runtime protection tools — but that’s just the start. Since most of these tools focus on vulnerability detection, organizations’ vulnerability management policy must also cover their prioritization and remediation strategy.
The Scope of a Vulnerability Management Policy
While the scope of a policy may vary depending on the size, type, and industry of an organization, a vulnerability management policy typically covers network infrastructure; servers; operating systems; virtual machines; cloud-hosted servers; database servers; databases; proprietary, third-party, and open source applications; company-owned devices; and more. It’s important to map out the scope and document it clearly to help avoid any uncertainty as to what is being monitored and how.
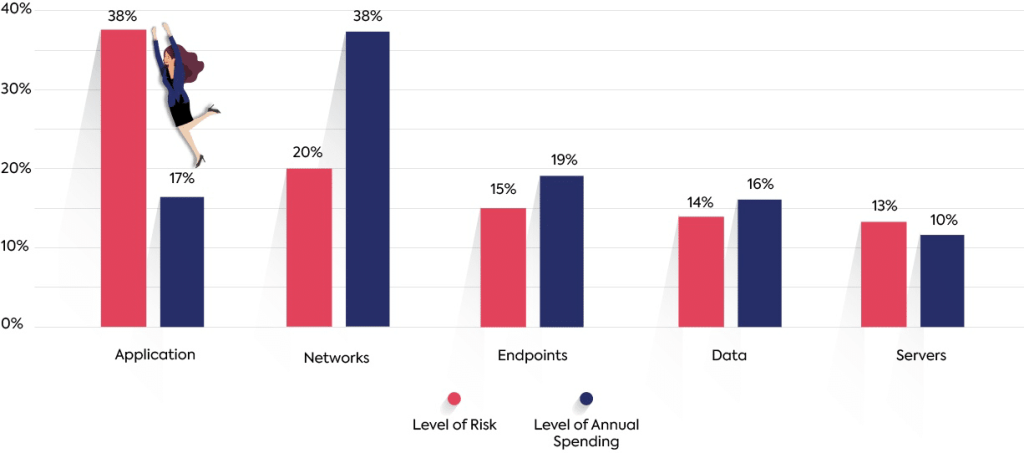
It’s also important to remember that each of the devices, environments, and frameworks that comprise an organizations’ system present a different type of risk. A research report from Ponemon Institute analyzed IT Security spend trends and found considerable gaps between the perceived level of risk for some of the attack vectors and the level of annual spending for the different protection layers. An effective vulnerability management policy will properly address each type of security threat and ensure that the right processes and tools are put in place to address the level of risk introduced by different vectors and layers.
Gap Between Security and the Allocation of Spending
Prioritization Is Key to Your Vulnerability Management Strategy
The goal of security teams is to fix all vulnerabilities detected in the company’s assets.
The problem is that this is nearly an impossible goal, which overloads the system and makes many teams frustrated with vulnerability management processes. Focusing on the issues that pose the biggest risk is the key to the successful implementation of new vulnerability management programs.
You need to ensure that clear guidelines are set for each asset regarding which vulnerabilities should be remediated and which should not. Many vulnerability management consultants can help define a risk-based prioritization procedure based on the company’s assets and market.


