Why Your DevOps Platform Needs a Security Partner to Safeguard Your Software

Table of Contents
The need for speed
Here at Mend.io, we work with businesses of different sizes and maturity across a wide variety of industry sectors, such as healthcare, finance, manufacturing, construction, media, software, and more.
One thing they have in common is that they are all involved in software development in one form or another. They use code and software components and dependencies within a DevOps environment to create both internal and customer-facing applications. And while applications grow more complex, the development deadlines grow ever tighter as the software development lifecycle (SDLC) accelerates.
Whether it’s reducing operational costs or innovating to keep ahead of the competition, software developers are under increasing pressure to deliver new applications quickly. To respond to this demand, they rely on modern software development techniques such as Agile, DevOps, containers, open source software, and continuous integration and delivery pipelines (CI/CD) to produce quality software at a faster pace.
The security challenge
Under such conditions, developers’ first priority is to create and ship new software and applications at speed. Unfortunately, this sometimes forces some corner-cutting when it comes to the often-cumbersome process of traditional application security.
However, the growth in software and application development comes with increased risk for exposure, in particular when using open-source components and dependencies. More vulnerabilities are emerging, and attacks on applications have increased. Today, applications are the top target and the biggest security risk that enterprise security teams face. The number of software supply chain attacks increased 650 percent from 2020 to 2021, and open source now comprises over 80 percent of the typical application code base.
With this in mind, neglecting or sidestepping security is no longer an option for organizations. Instead, companies need a modern approach to security that enables developers to apply security measures quickly and easily, and shift the process left by implementing security earlier in the SDLC. In short, application development teams need an efficient way to identify and fix application vulnerabilities without slowing down CI/CD pipelines or the pace of software delivery.
The good news is that with the right tools, any software developer can remediate open-source vulnerabilities quickly.
What are the right tools?
To achieve this, developers need a solution that offers an enterprise-ready DevOps environment and transforms it into DevSecOps by integrating the security directly into the SDLC. Such integration will create a robust CI/CD capability that ensures software and applications can be at speed while still meeting both developer and application security requirements. For example, Mend has partnered with CloudBees CI, the leading DevOps solution for large organizations that need powerful risk mitigation, compliance, and governance capabilities, to enable users to:
- Scan applications to find open-source software vulnerabilities
- Provide zero false positive alerts thanks to Mend’s patented Reachability Path Analysis
- Show developers exactly how to remediate their open-source vulnerabilities
- Identify and block malicious third-party packages from entering your code base
How does it work?
CloudBees’ CI enhanced support covers the integration with Mend, offering centralized management and validation of plugins and integrations with third-party technologies. Built-in security supports single sign-on, role-based access controls, and a trusted version of Jenkins. It also offers elastic scaling at both the infrastructure layer and the organization layer and ensures that there are no bottlenecks. The proprietary CloudBees compliance features allow you to enforce organizational standards such as the separation of duties models. It achieves all this with the following process:
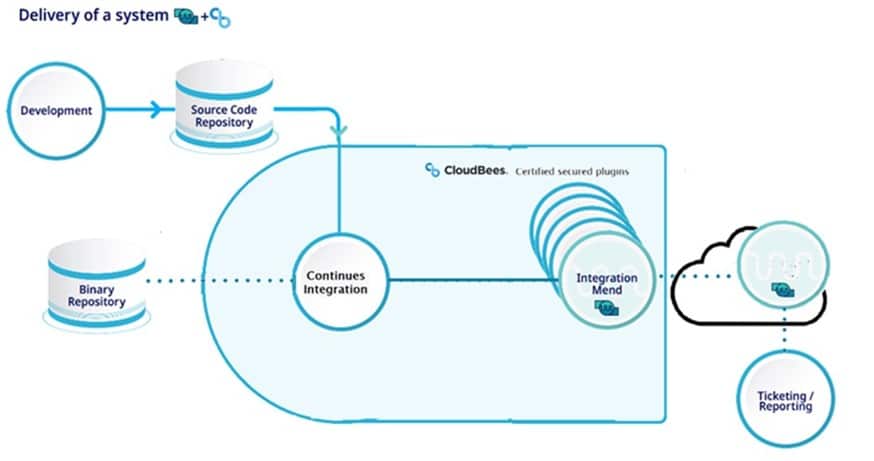
- CloudBees CI triggers the code scan by Mend. Scans are performed locally. Your source code always stays on-premises.
- Results of each scan are sent to Mend’s SaaS elastic scalable cloud for analysis, requiring no additional deployment resources or monitoring.
- Mend vulnerability analysis is either displayed on the Mend web-based user interface or piped into your existing vulnerability collection system or ticketing system via API. Mend Prioritize shows you which open-source vulnerabilities are attackable, which are not, and therefore which should be fixed first.
- CloudBees CI completes the build process and uploads the image created to the Binary Repository or breaks the build based on Mend’s policy configuration.
Benefits
This partnership illustrates an effective way of seamlessly offering security inside a DevOps environment. Organizations are focused on continuous innovation and their developers seek platforms, solutions, and tools that will enable them to deliver scalable, compliant, and secure new software and applications. Furthermore, they want their user experience to be easy, fast, and thoroughly reliable.
CloudBees is all about facilitating CI/CD and DevOps. In other words, speeding up software delivery in a modern way for large enterprises and medium-sized businesses. It ably fulfills these DevOps requirements but needs a strong security partner to meet users’ growing demand for extending DevOps into DevSecOps. The partnership with Mend integrates open source security directly into the DevOps CI delivery platform so that you can:
- Completely automate the process of scanning applications for vulnerabilities, making it simple to implement
- Reduce their application attack surface
- Find vulnerabilities and prioritize which ones to fix first
- Save time. Developers can reduce the amount of time that they would otherwise spend on remediating vulnerabilities by up to 80 percent
- Block supply chain attacks, identify malicious open-source software packages, and block them before they have a chance to pollute your code base
- Enforce compliance policies with automated testing and reject builds that don’t pass your security criteria
- Ensure that your open source software, components, and dependencies comply with licenses and reject those builds that violate your license policies
The imperative to innovate is huge, and this drives the pace and volume of software and application development. However, alongside this acceleration in innovation comes the growth in the potential attack surface and a steep increase in vulnerabilities, which can allow serious threats to infiltrate your codebase. Case in point: the Equifax security breach of 2017, which exposed the personal information of 147 million people and resulted in the company paying settlement costs of up to $425 million. Or more recently, the Log4j vulnerability, whose impact was so huge that Jen Easterly, director of the U.S. Cybersecurity and Infrastructure Security Agency, described it as “the most serious vulnerability I have seen in my decades-long career.”
It’s therefore more vital than ever to safeguard your DevOps environment. The value of security is high because experience has shown us that the cost of lax security will be higher.
If you’d like to improve the security of your application development with Mend and CloudBees, check out our solution brief here.





